DESCRIPTION LAST UPDATED: 2024-03-20
DEFAULT SEVERITY LEVEL: HIGH
This report contains information about hosts that can be abused in a novel type of Denial-of-Service (DoS) attacks: application-layer loop DoS. Such loop DoS attacks become possible if two network services indefinitely respond to each other’s messages. The hosts contained in this file have been found to cause such endless loop patterns. If you receive this report for your network or experience abuse of such hosts, consult the advisory on how to mitigate the resulting attacks.
The application-layer loop DoS vulnerabilities were discovered by the security researchers Yepeng (Eric) Pan and Christian Rossow from the CISPA Helmholtz Center for Information Security in Germany.
To illustrate the attack vector, imagine two DNS resolvers that respond with an error message when receiving an error message as input. If an error as input creates an error as output, and a second system behaves the same, these two systems will keep sending error messages back and forth — indefinitely. The figure below shows such an example we identified among real DNS servers. An attacker can cause a loop among two faulty DNS servers by injecting a single, IP-spoofed DNS server failure message. Once injected, the servers continuously send DNS error messages back and forth, putting stress on both servers and any network link connecting them.
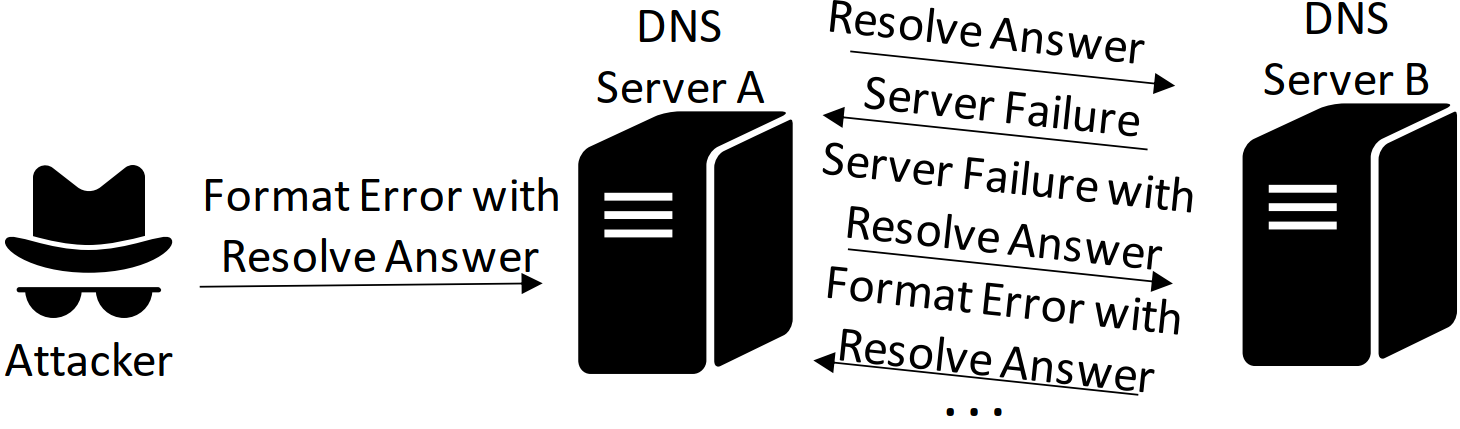
Loop DoS attack illustration
If you receive the report for your network, we would appreciate feedback as to the vendor/product involved. This is necessary for us to alert vendors to patch this vulnerability. You can report feedback via e-mail to loop-dos (at) shadowserver.org or simply Contact Us.
Severity levels are described here.
Filename prefix: scan_loop_dos .

