Shadowserver Special Reports are a NEW type of free, one off report. They do not cover a specific time period. We will send out Special Reports whenever we are able to share one-time, high value datasets that we feel should be reported responsibly for maximum public benefit. Although the events included in these Special Reports will fall outside of our usual 24 hour daily reporting window, we believe that there would still be significant benefit to our constituents in receiving and hopefully acting on the retrospective data.
This new Special Report – Vulnerable Exchange Servers Special Report #4 – is our fifth in a series of Special Reports on the rapidly developing situation related to ongoing attacks globally against the recently patched zero-day CVE-2021-26855, CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065 vulnerabilities in Microsoft Exchange Server. You can read blog posts covering the previous installments here:
- HAFNIUM attributed Exchange victims (2021-02-26 to 2021-03-03, pre-patch release)
- Exchange Scanning #1 – mass exploitation (2021-03-09, post-patch release)
- Exchange Scanning #2 – confirmed web shells (2021-03-12, post-patch release)
- Exchange Scanning #3 – potentially vulnerable servers (2021-03-13 to 2021-03-14, post-patch release)
During the past week, mass attacks against vulnerable Microsoft Exchange servers have been widely reported by multiple threat actor groups. Unfortunately the types of attacks have quickly become much easier to perform, after working CVE-2021-26855 ProxyLogon Exploit exploit code was recently published online. This has moved most incidents from APT to mainstream cybercrime activities, including ransoming and cryptocurrency mining.
Having already partnered with KryptosLogic on our one-off Special Report #2 that identified publicly exposed web shells, they have once again kindly offered to share the data from their latest Internet wide scan for vulnerable Microsoft Exchange servers, which was performed on 2021-03-14.
Their data set is composed of:
- 59218 different potentially vulnerable Microsoft Exchange servers identified on 59142 unique IP addresses corresponding to 6501 different Autonomous System Numbers (ASNs), geo-locating to 211 different countries.
For comparison, the data set which we just distributed for the previous one-off Special Report here covered the period 2021-03-13 to 2021-03-14 and was composed of:
- 73608 different potentially vulnerable Microsoft Exchange Servers identified by IP address or DNS name on 63115 unique IP addresses corresponding to 6664 different Autonomous System Numbers (ASNs), geo-locating to 211 different countries.
Although similar in goal, each data set was generated at a different time, with a different test methodology and run from a different location. For people wondering about the degree of overlap (and the need for multiple organizations to be performing similar parallel research), if we compare both data sets we find that:
- 50462 potentially vulnerable Microsoft Exchange servers were common to both data sets
- 12653 instances only appeared in the first set
- 8680 instances only appeared in this second (Kryptoslogic’s scan) set
So it seems at this stage that having different network vantage points and using vulnerability detection methodologies provides alternative but valid and useful information to support network defenders and incident responders in triaging these remaining potentially vulnerable Microsoft Exchange servers.
Both datasets have been distributed as one-off Special Reports to 120 National CSIRTs in 148 countries and over 5900 network owners. Due to the high risk that most have already been compromised at least once, we strongly encourage network owners and National CERT/CSIRTs to urgently remediate and patch/rebuild all impacted victim systems immediately.
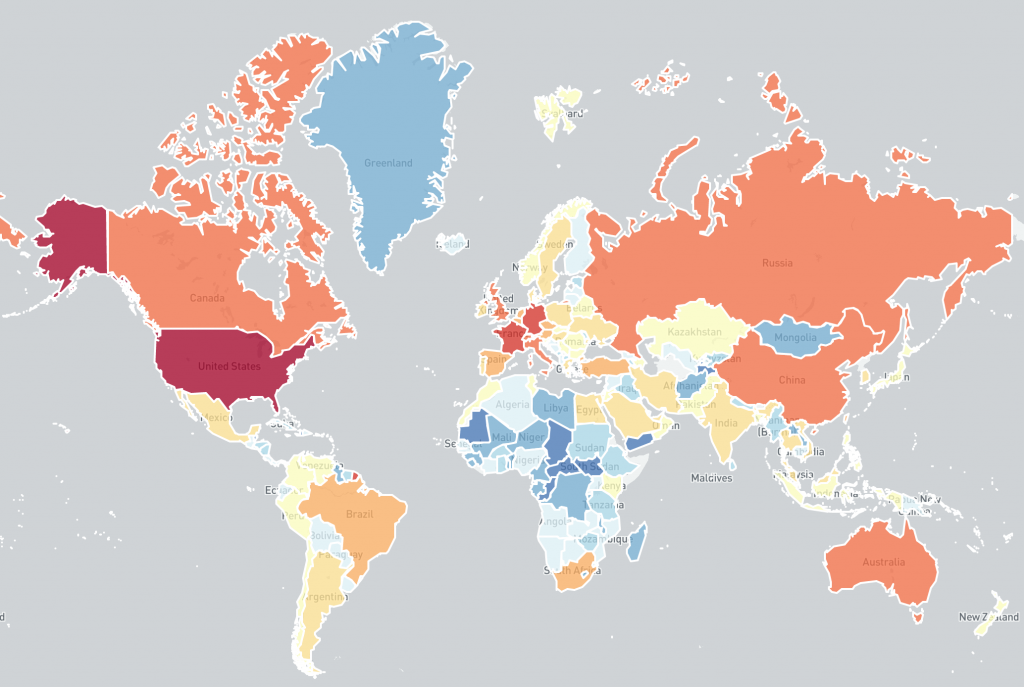
Country level distribution of potentially vulnerable Microsoft Exchange Servers in this scan on 2021-03-14 (log scale):
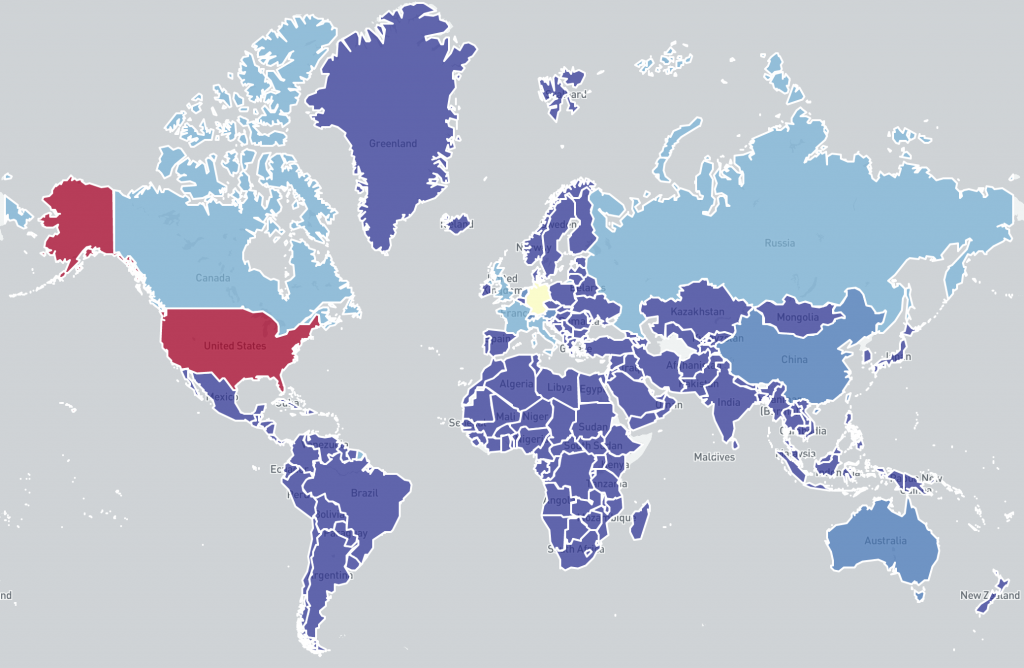
Country level distribution of potentially vulnerable Microsoft Exchange Servers in this scan on 2021-03-14 (linear scale):
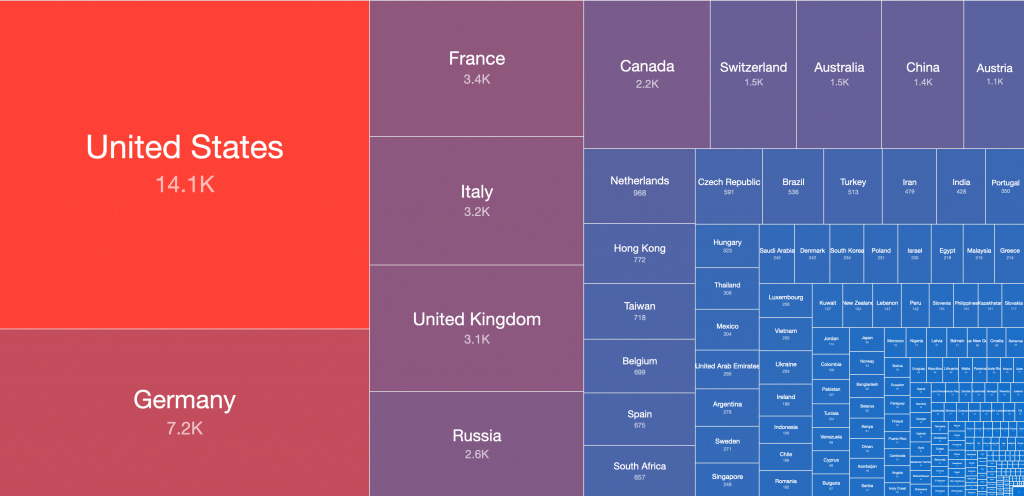
Country level distribution of potentially vulnerable Microsoft Exchange Servers in this scan on 2021-03-14 (treemap):
You can find more detail on the format of the new Special Report here.
Remediation advice for Microsoft Exchange Server operators has been provided by CISA. Microsoft have released tools for checking Exchange servers for evidence of exploitation. You can also use the online CheckMyOWA resource to check if your Exchange Server has appeared in their data.
If you have missed this Special Report because you were not yet a subscriber to our free daily network reports, do not worry: simply subscribe for your network or country now and specifically request all recent Shadowserver Special Reports. We will resend the Special Report specifically for your network or country (for National CERT/CSIRTs).
If you have a data set which you feel could also be of benefit to National CERT/CSIRTs and network owners world-wide to help protect victims of cybercrime, please get in touch and discuss the options for using Shadowserver’s proven reporting systems for distribution and remediation.
We hope that the new Shadowserver Special Reports will be a useful additional free tool in helping network defenders identify victims and better protect their networks and the entire Internet. Please contact us if you have any questions.