As covered in our previous blog post, on Tuesday 29th August 2023, the US Department of Justice (DoJ) and US Federal Bureau of Investigation (FBI), together with other global law enforcement partners, announced a disruption action against the Qakbot botnet.
This activity has been widely reported on, and involved the FBI deleting the Qakbot malware from infected victim computers under US court order (to reduce the risk of further harm).
Since the Qakbot malware was deleted from the victim systems during this law enforcement action, the traditional sinkhole-based approach of detecting infected devices via observed command and control traffic, and then reporting these victim systems out to network owners and National CSIRTs for remediation, will not be possible.
However, as part of their operation, the FBI acquired a copy of the threat actor’s database of historical Qakbot infections, which covered the period July 2019 to August 2023. This database contains a record of over 700,000 discrete Qakbot bot infections, covering victims systems in 230 countries.
At the request of the FBI, The Shadowserver Foundation are sharing elements of this dataset with system defenders in the following manner:
- National CSIRTs will receive a one-off ‘Special Report’ about historical Qakbot infected devices in their country, containing victim IP addresses and supporting meta data to allow system identification, filtered by geographical region. Shadowserver currently has 201 nCSIRTs in 175 countries and territories receiving our data globally, and are working to help countries who do not yet have a National CSIRT to develop that capability.
- Network owners will receive a one-off ‘Special Report’ about historical Qakbot infected devices in their own networks of responsibility, containing victim IP addresses and supporting meta data to allow system identification. Over 8000 organizations are currently directly subscribed to Shadowserver’s free data network reports. This includes organizations responsible for more than 59% of IPv4 network space in the United States.
This Qakbot Historical Bot Infections Special Report will be disseminated overnight on September 7th 2023. The supporting web page for this Special Report can be found here.
Anyone who has not yet signed up for Shadowserver’s free daily network reports can subscribe and register their network space here. If you sign up after the dissemination date, you can request a back dated Qakbot Historical Bot Infections Special Report for your network (or country, for new nCSIRTs).
This reporting is provided in partnership with the FBI, at no cost, as a public benefit service, and is part of Shadowserver’s mission to make the Internet more secure for all users.
Secondary Malware Infections
It is important to note that Qakbot has been used to drop additional malware on infected systems, so although the FBI have deleted live Qakbot infections, other malware infections may still be active on these systems and require further local remediation efforts. These victim systems may also have been used in historic or recent intrusions and ransomware incidents.
We are aware of cases where Qakbot was a secondary infection to Emotet and has been seen in conjunction with other criminal activity (such as the unauthorised deployment of Cobalt Strike, likely as a precursor to ransomware attacks). We therefore ask all recipients of these Special Report notifications to not just consider Qakbot in their incident response activities, but also the possibility of secondary infections and/or indication of wider lateral movement.
If you have received a Qakbot Historical Bot Infections Special Report and you need more information about a specific infection, please contact us and we can provide more details, or put you in touch with the law enforcement investigating officers, if required.
It should be noted that some IP addresses can be associated with multiple Qakbot infections over that time period. A subset of the recorded Qakbot “victims” are likely to actually be security researchers or sandbox systems, but these events have been included for completeness (hopefully, those people know who they are, and what they have been doing).
Qakbot Historical Bot Infections – Data Analysis
We are publicly sharing some high level analysis of the Qakbot historical bot infections dataset from the period between July 2019 to August 2023. For each of the images below you can click on it to view a higher resolution version.
The world maps below show the total number of Qakbot infections logged per country:
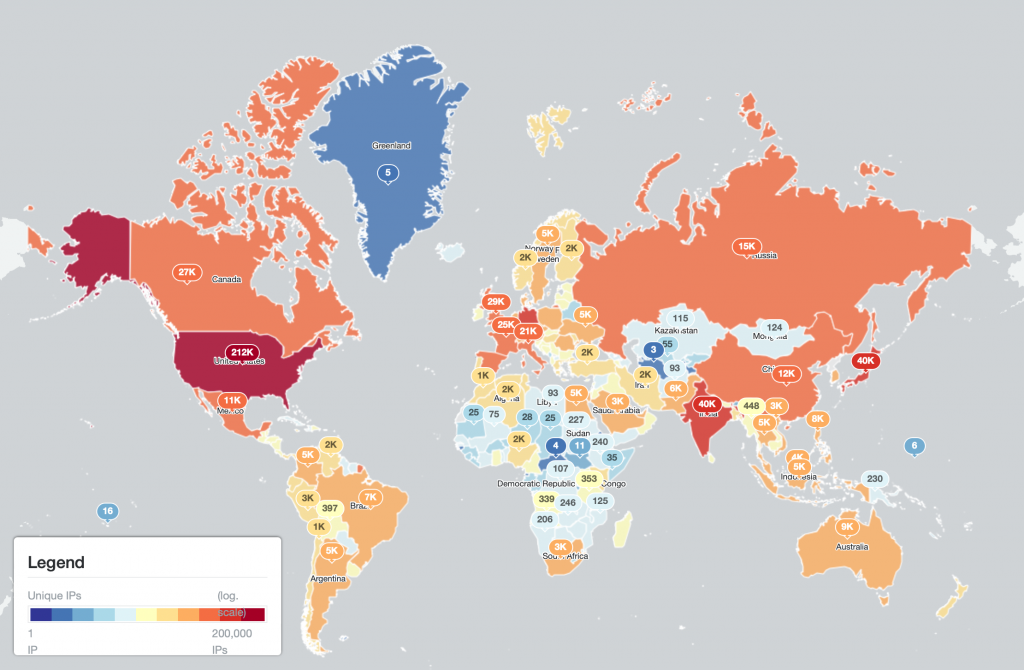 (Qakbot infections per country – linear scale)
(Qakbot infections per country – linear scale)
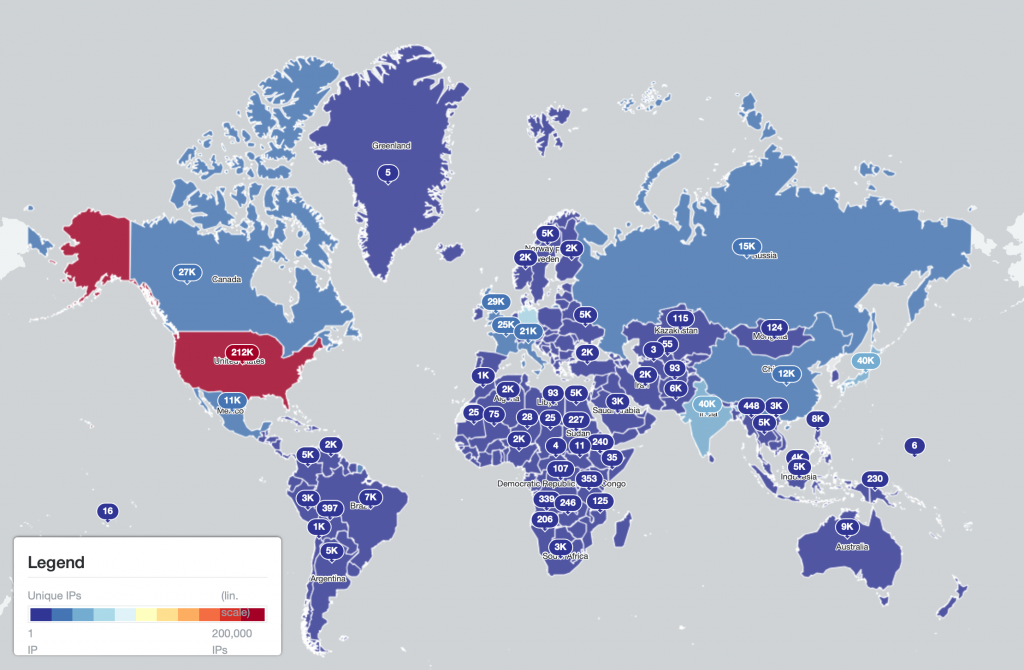 (Qakbot infections per country – logarithmic scale)
(Qakbot infections per country – logarithmic scale)
The IP-geolocated locations of each logged Qakbot infection (note that since there can be multiple bot infections behind a single IP address, these visualizations show unique geolocated IP addresses and may therefore under-represent the actual victim distribution globally):
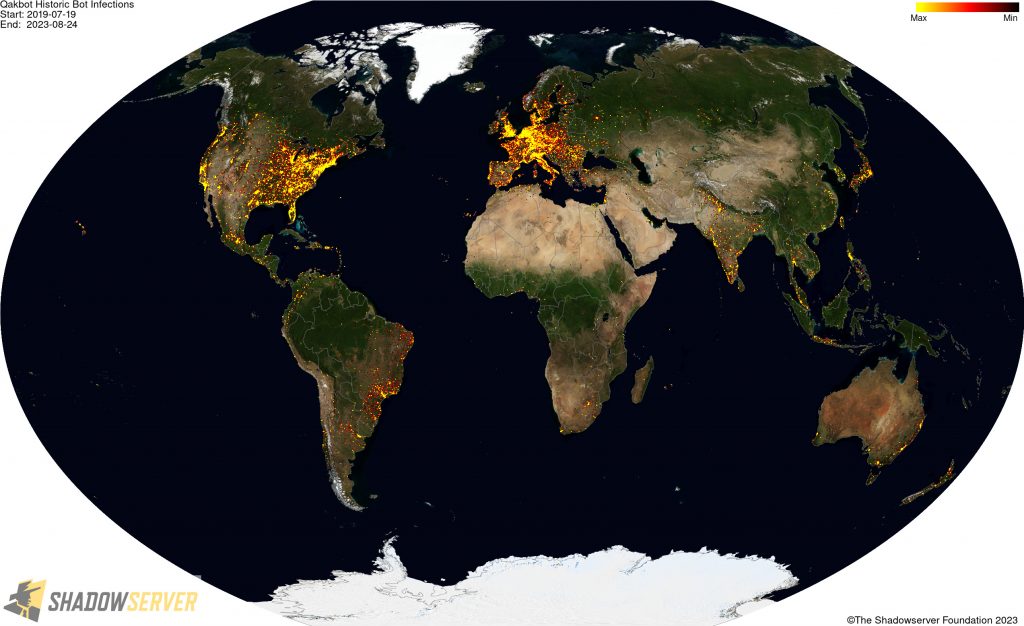 (IP-geolocated Qakbot infections – Worldwide)
(IP-geolocated Qakbot infections – Worldwide)
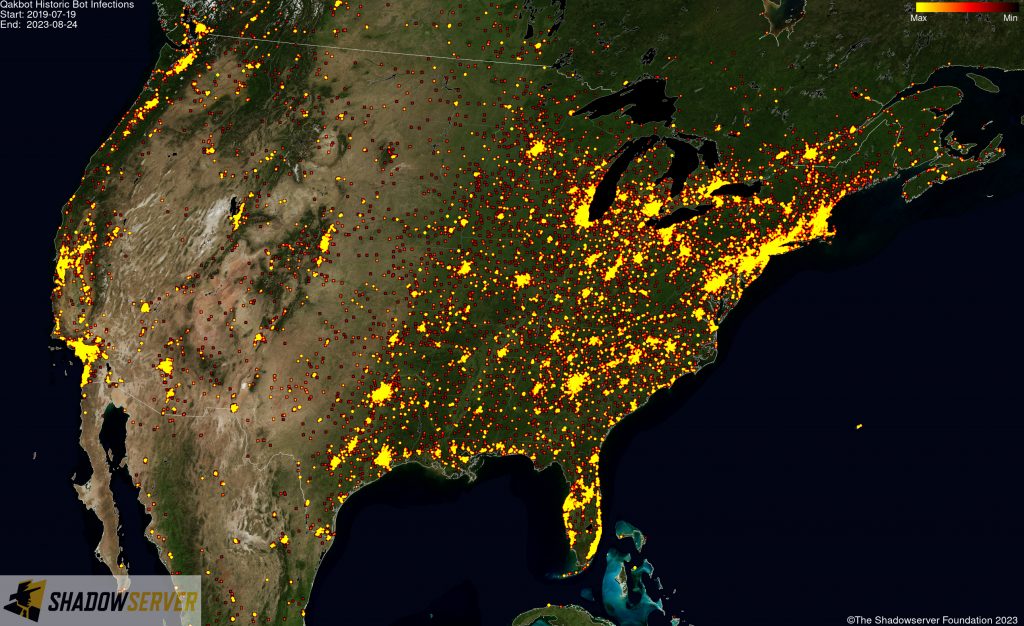 (IP-geolocated Qakbot infections – USA)
(IP-geolocated Qakbot infections – USA)
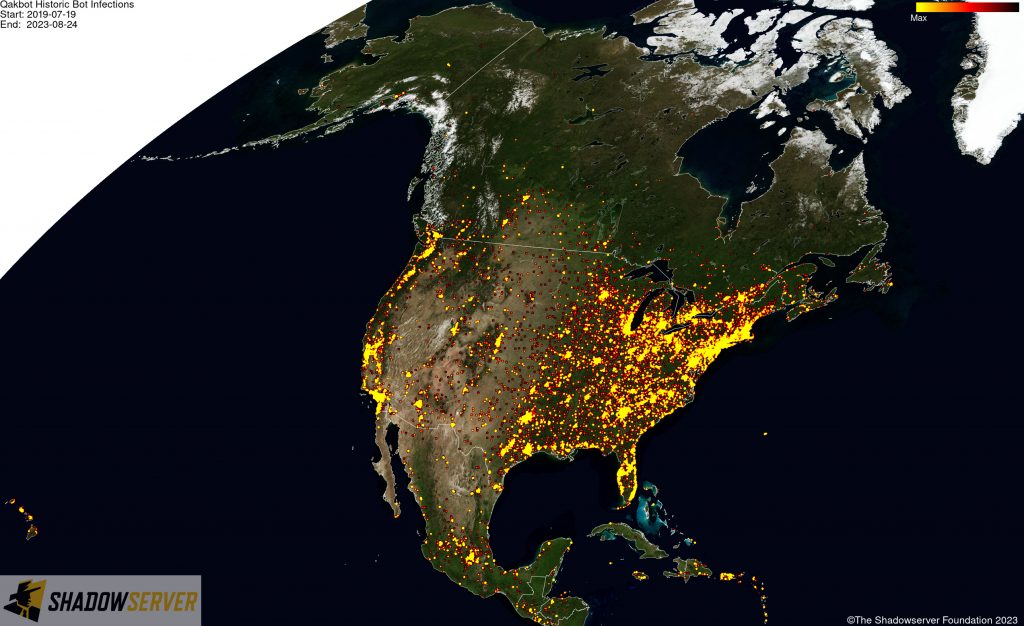 (IP-geolocated Qakbot infections – North America)
(IP-geolocated Qakbot infections – North America)
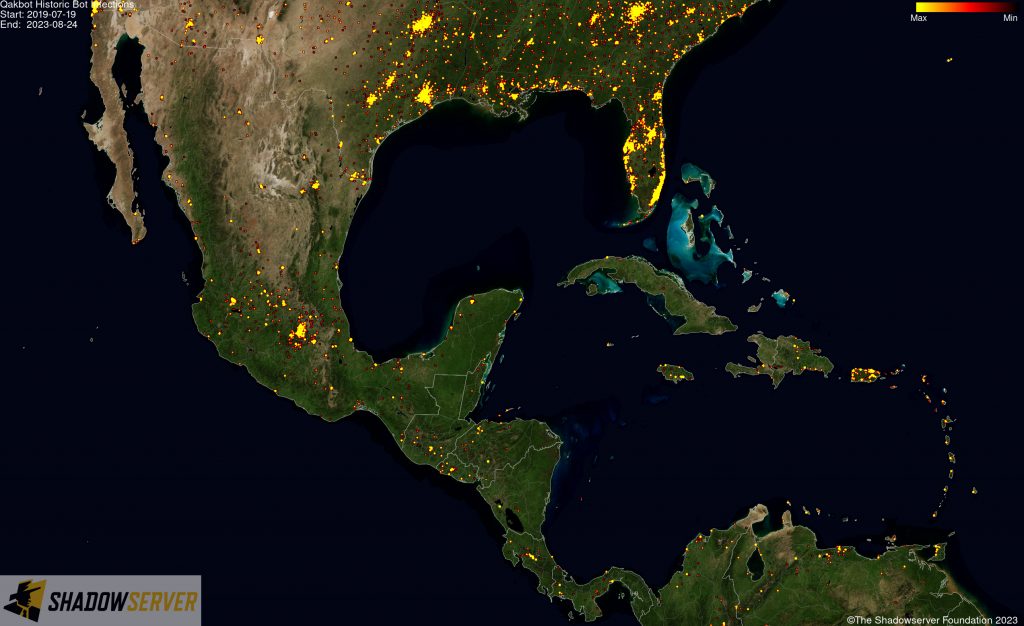 (IP-geolocated Qakbot infections – Central America)
(IP-geolocated Qakbot infections – Central America)
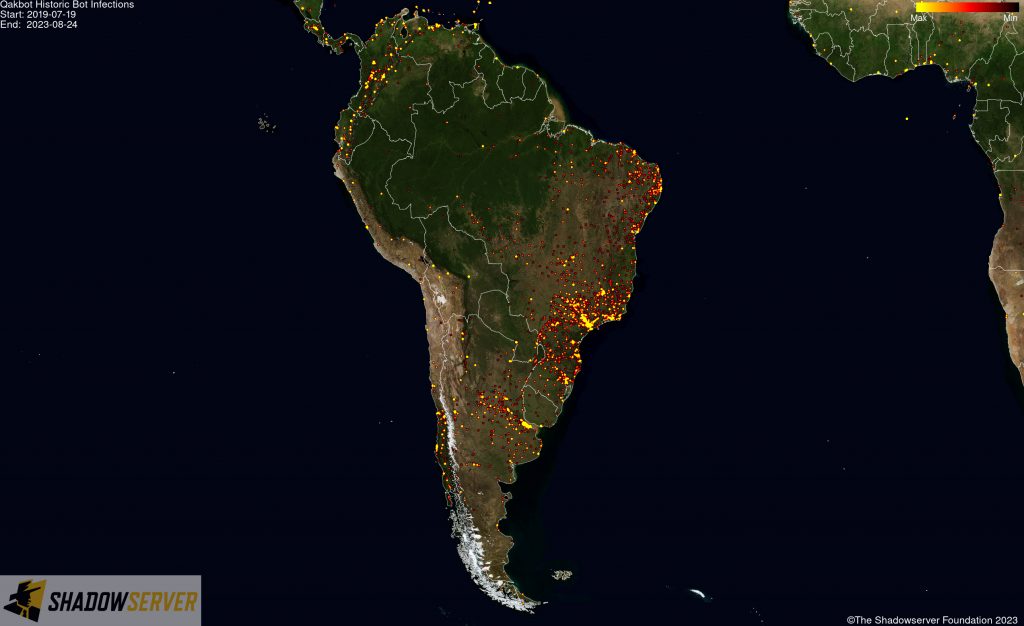 (IP-geolocated Qakbot infections – South America)
(IP-geolocated Qakbot infections – South America)
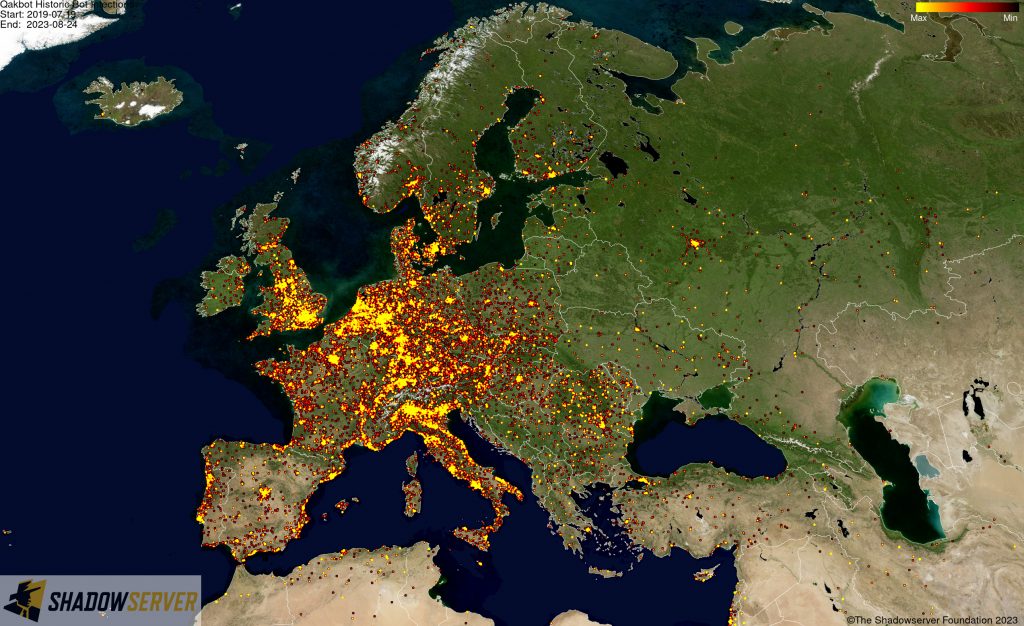 (IP-geolocated Qakbot infections – Europe)
(IP-geolocated Qakbot infections – Europe)
 (IP-geolocated Qakbot infections – UK/Europe)
(IP-geolocated Qakbot infections – UK/Europe)
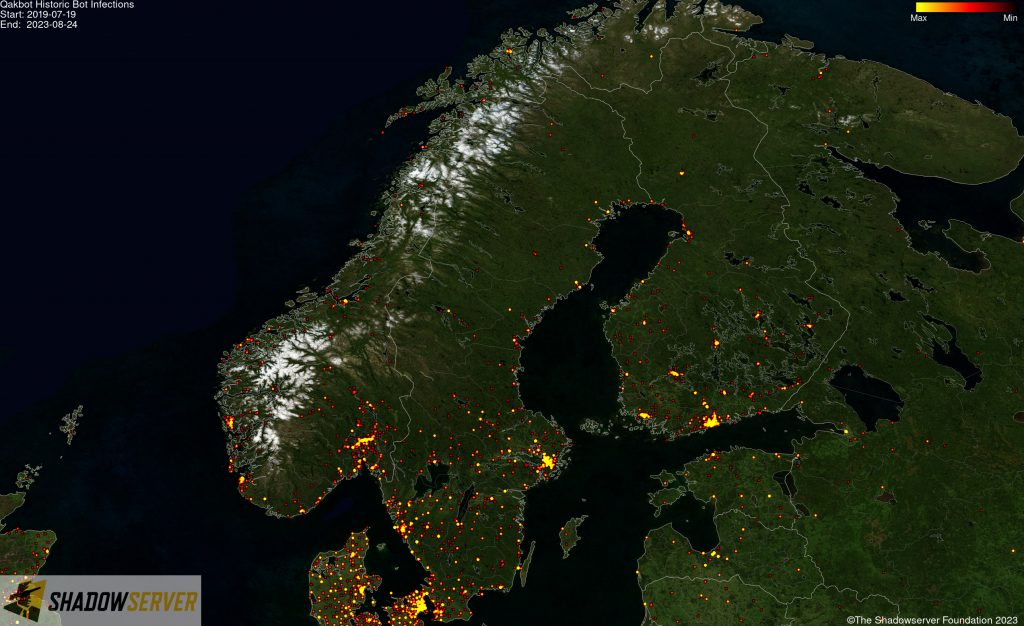 (IP-geolocated Qakbot infections – Scandinavia)
(IP-geolocated Qakbot infections – Scandinavia)
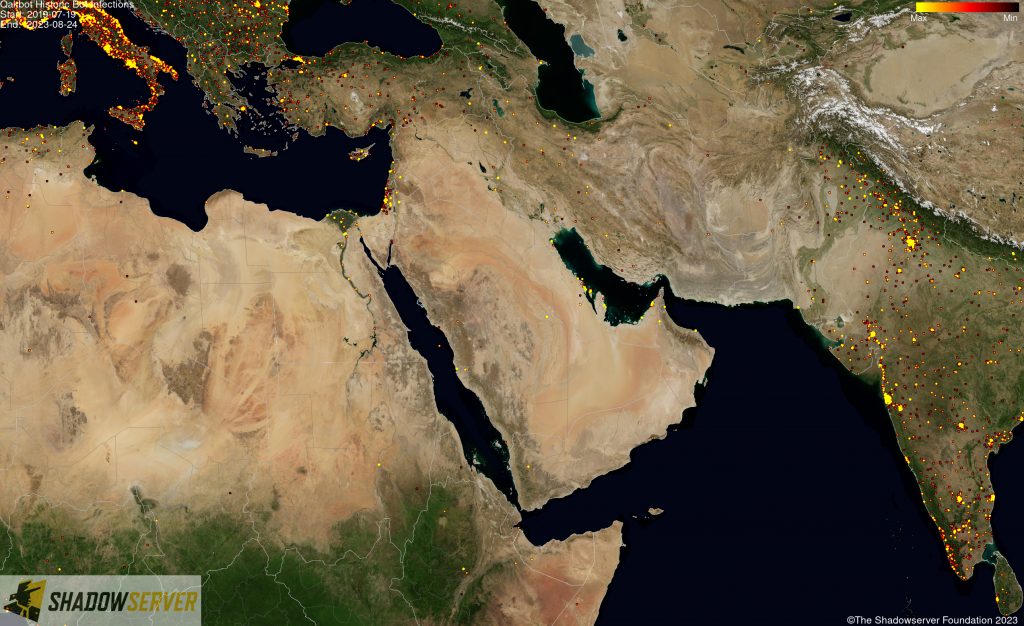 (IP-geolocated Qakbot infections – Middle East)
(IP-geolocated Qakbot infections – Middle East)
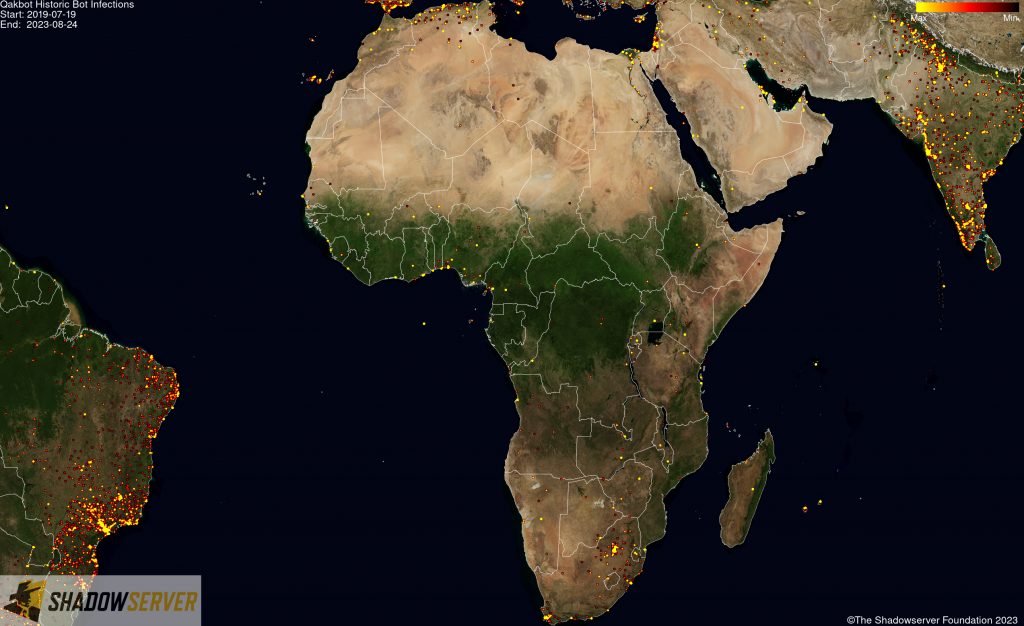 (IP-geolocated Qakbot infections – Africa)
(IP-geolocated Qakbot infections – Africa)
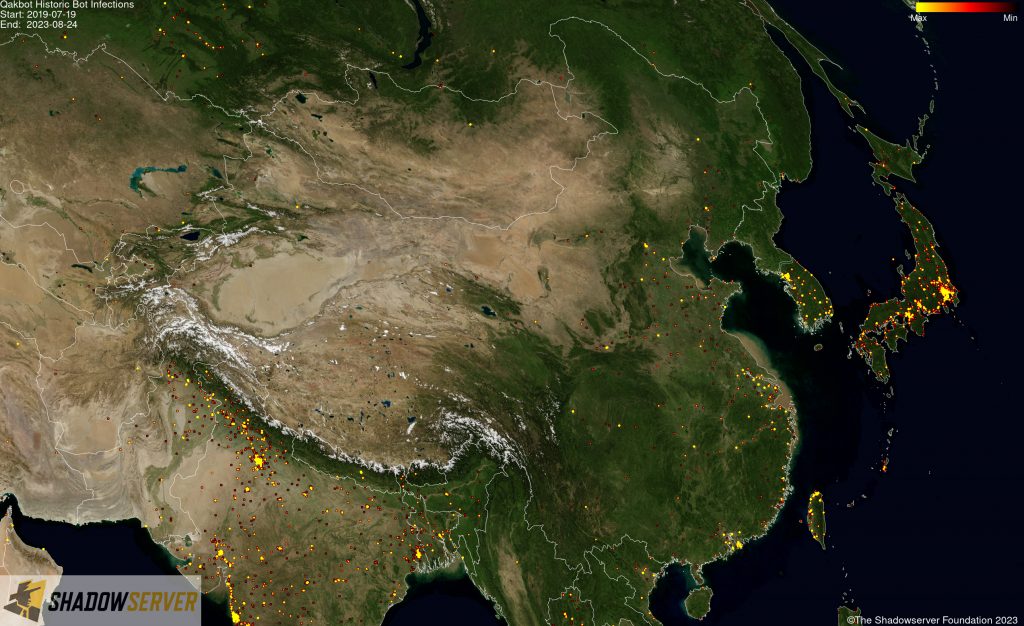 (IP-geolocated Qakbot infections – East Asia)
(IP-geolocated Qakbot infections – East Asia)
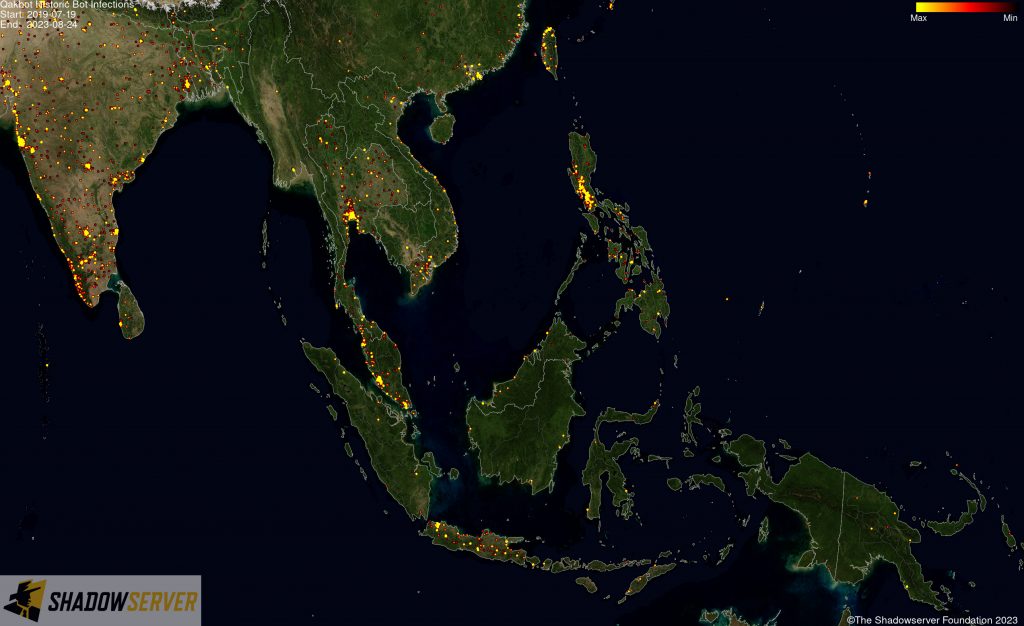 (IP-geolocated Qakbot infections – Oceania)
(IP-geolocated Qakbot infections – Oceania)
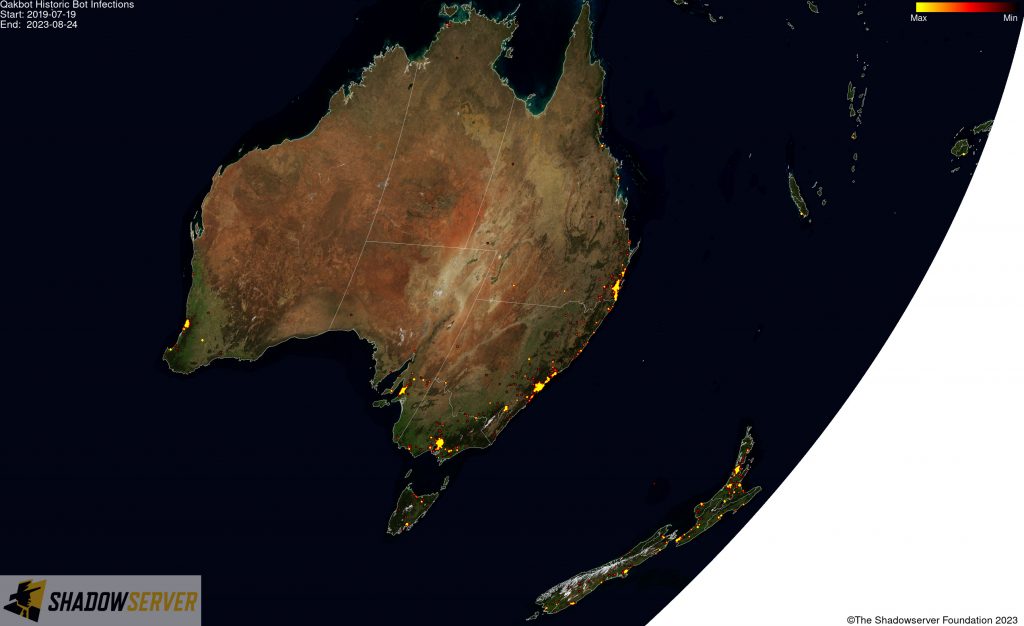 (IP-geolocated Qakbot infections – Australia/New Zealand)
(IP-geolocated Qakbot infections – Australia/New Zealand)
Looking at the data in a different way, the tree map below shows the relative ratio of Qakbot infections logged per country to the total. Note that a small number (398) of IP addresses do not geolocate to a country, so the displayed number is slightly lower than the actual total:
 (Qakbot infections per country)
(Qakbot infections per country)
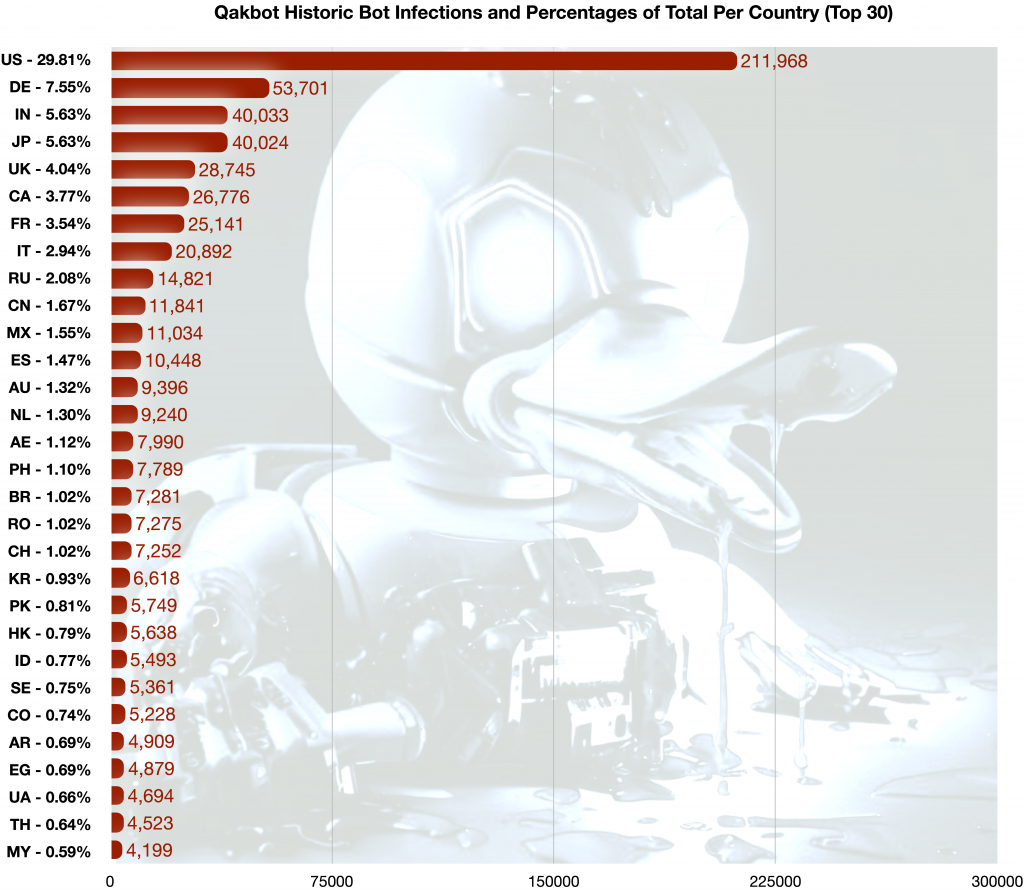
In chart form, the total number of Qakbot infections logged during the period July 2019 to August 2023, and the percentage of the total per country, was:
(Qakbot infections and percentage of total per country)
If you have any questions, please contact us, although there may be limitations on what information can be shared at this moment due to the ongoing LE investigations.