Non-profit consortium launches national scale Cyber Resilience pilot to assess the cyber threat landscape for the NGO sector in The Netherlands
April 4, 2024
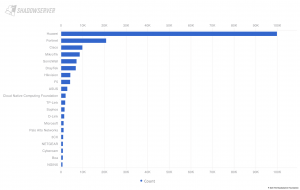
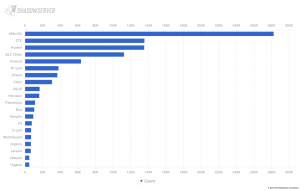
A non-profit consortium – consisting of The Hague Humanity Hub, the CyberPeace Institute (CPI), Connect2 Trust Foundation and The Shadowserver Foundation, co-funded by Rijksdienst voor Ondernemend Nederland (RVO), will produce a national level assessment of the cyber threat landscape for NGOs, while measuring the impact and harm of cyber threats on the sector.