Help Net Security, December 5, 2024
In this Help Net Security interview, Piotr Kijewski, CEO of The Shadowserver Foundation, discusses the organization’s mission to enhance internet security by exposing vulnerabilities, malicious activity, and emerging threats. Kijewski explains the foundation’s automated efforts to track and disrupt cybercrime.
By providing actionable intelligence we help equip CSIRTs and network defenders worldwide with the information needed to secure their networks and/or constituencies. We also provide free technical support to law enforcement cybercrime disruption operations. We provide cybersecurity capacity building services around the world (typically funded through various grants, such as from the UK Foreign, Commonwealth and Development Office – FCDO) in areas of threat detection, cyber threat intelligence and incident response.
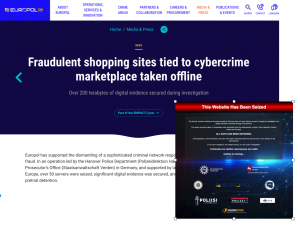
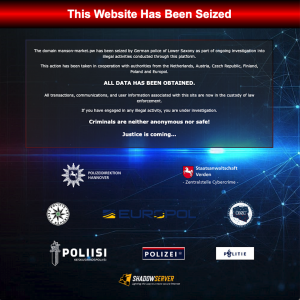
Shadowserver’s free daily network reports help provide organizations with a baseline of timely, actionable and often unique cyber threat intelligence – even for those organizations without big budgets.