DESCRIPTION LAST UPDATED: 2025-01-28
DEFAULT SECURITY LEVEL: MEDIUM
This report contains information about a vulnerability that allows new Denial-of-Service (DoS) vulnerabilities. This vulnerability originates from hosts that accept tunnelling packets such as IPIP, GRE, 6in4 and 4in6 without authenticating the source IPv4 or IPv6 address. Attackers can exploit these hosts as proxies to conceal their identity when conducting attacks and spoof the source IP address of packets.
If you receive this report for your network or experience abuse of such hosts, visit the TunnelTester GitHub repository for more information, including advise on how to mitigate the resulting attacks.
These vulnerabilities were discovered by Angelos Beitis and Mathy Vanhoef of the DistriNet Reseach Unit at KU Leuven University in Belgium.
As an illustration, assume a vulnerable tunnelling host that decapsulates and forwards tunnelling packets without authenticating the sender, i.e., it accepts packets from any source. The attacker can send a tunnelled packet where the outer header is sourced from the attacker and destined towards the vulnerable host. Subsequently, the inner header will have the vulnerable host as the source and the victim as the destination. The vulnerable host will receive this packet, decapsulate the outer header and forward the inner packet to the victim. As a result, the victim will believe the packet originated from the vulnerable host.
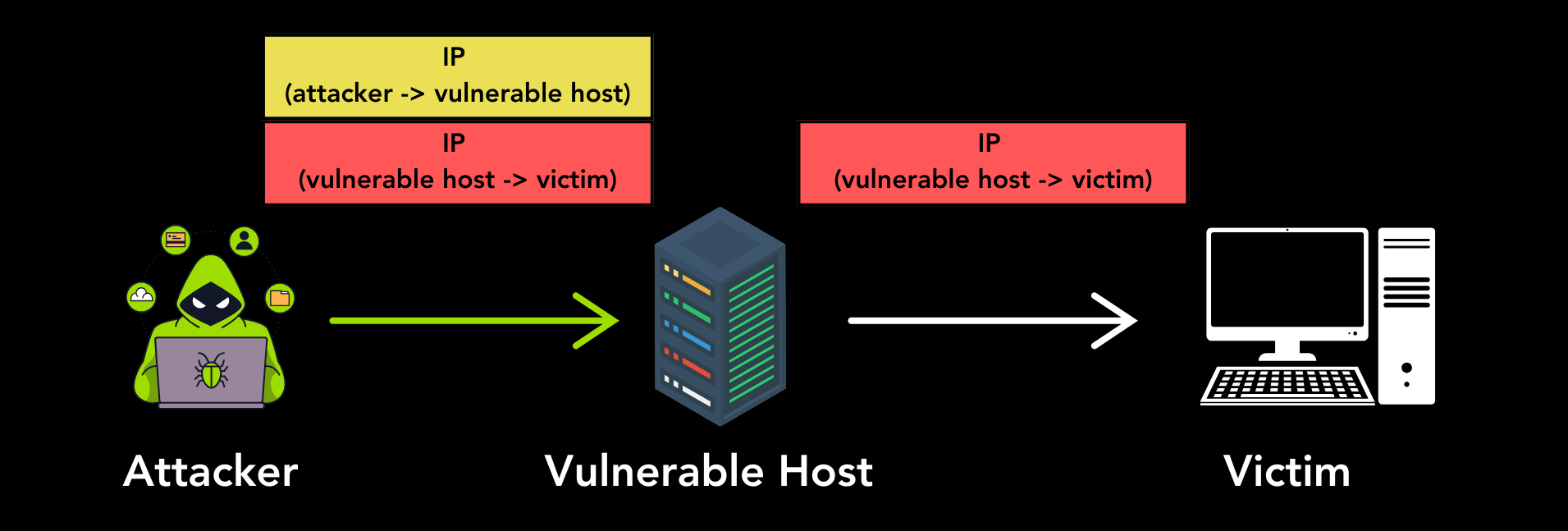
IP tunnel attack overview
You can track our results on our Dashboard (select source ip_tunnel for IPv4 data and/or ip_tunnel6 for IPv6 data, then select a tag or group of tags that represent IPIP/GRE/4in6/6in4).
Severity levels are described here.
For more information on our scanning efforts, check out our Internet scanning summary page.
This report has an IPv4 and IPv6 version.
Filename(s): scan_ip_tunnel, scan6_ip_tunnel

