Introduction
 2024 was another banner year for The Shadowserver Foundation. As we celebrated the 20th anniversary of our founding in 2004, we continued to be a global leader in cybersecurity, providing free public benefit services to the community in pursuit of our nonprofit mission to make the Internet safer and more secure for everyone.
2024 was another banner year for The Shadowserver Foundation. As we celebrated the 20th anniversary of our founding in 2004, we continued to be a global leader in cybersecurity, providing free public benefit services to the community in pursuit of our nonprofit mission to make the Internet safer and more secure for everyone.
We would like to take this opportunity to thank all of our supporters, particularly the United Kingdom’s Foreign, Commonwealth and Development Office (UK FCDO), Craig Newmark of Craig Newmark Philanthropies, all of our Shadowserver Alliance partners, and those who supported us through donations, voluntary invoicing, and funded projects. Without your support, our many successes of 2024 would not have been possible.
While our contributions to the community take many forms, the key pillars of our public benefit services include:
– Free, Actionable Cyber Threat Intelligence
Our free, daily cyber threat intelligence, in the form of network remediation reports, helps organizations and National CSIRTs (Computer Security Incident Response Teams) around the world to secure their networks. These reports provide both an Early Warning Service, identifying publicly exposed, misconfigured, and vulnerable devices on a network to be patched before a breach occurs, and a Victim Notification Service, identifying compromised devices on a network to be remediated before further exploitation, such as a ransomware attack, can occur. Each detected issue is designated with a severity level to help organizations and National CSIRTs prioritize patching and other remediation actions to be taken to achieve a more secure network. Our reports include the latest high-risk vulnerabilities and unique victim data sets shared with Shadowserver by Law Enforcement.
– Global Cybersecurity Capacity Building
We provide cybersecurity capacity building (CCB) services in the areas of threat detection, cyber intelligence, and incident response. By helping to secure networks globally, we reduce the opportunity for bad actors, including cybercriminals and nation-state threat actors, to proxy their attacks using compromised networks.
– Free Support to Law Enforcement
We provide free technical assistance to many of the world’s most significant cybercrime disruption operations, quarantining millions of malicious domains using our special purpose DNS registrar, the Registrar of Last Resort (RoLR). We conduct ‘sinkholing’ – the process of disrupting the connections between malware-infected devices and threat actor-controlled servers, and redirecting that traffic safely to our sinkhole servers – to actively protect victims from further exploitation. We then use our Victim Notification capabilities to help Law Enforcement and National CSIRTs notify millions of victims per day that their devices have been compromised by threat actors, encouraging remediation.
World’s Largest Provider of Free, Actionable Cyber Threat Intelligence
During the past year, Shadowserver continued to increase the size of our constituency, and expand the depth and breadth of our cybersecurity threat coverage.
– Increased Subscribers to our Network Remediation Reports
In 2024, we increased our number of free daily network remediation report subscribers to more than 9,000 organizations globally and 201 National CSIRTs covering 175 countries.
Each year since 2021, we have steadily increased the percentage of network owners on each continent subscribing to directly receive our free daily network remediation reports about their IP space. These figures do not take into account the tens of thousands of network owners who do not subscribe to our network remediation reports directly, but rather do receive the information from their National CSIRT, by enrolling in Early Warning Programs such as the one offered by the UK’s National Cyber Security Centre (NCSC)
Percentage of direct IPv4 daily network report subscriptions per continent
| Continent | 2021-12-31 | 2022-12-31 | 2023-12-31 | 2024-12-31 |
| Africa | 7% (13%) | 23% (40%) | 41% (71%) | 44% (77%) |
| Asia | 15% (20%) | 25% (32%) | 28% (35%) | 29% (36%) |
| Europe | 50% (50%) | 57% (57%) | 60% (58%) | 63% (60%) |
| North America | 53% (55%) | 54% (56%) | 57% (60%) | 59% (67%) |
| South America | 6% (9%) | 11% (17%) | 11% (18%) | 33% (52%) |
| Oceania | 40% (40%) | 64% (63%) | 65% (63%) | 65% (61%) |
| Globally | 36% (41%) | 42% (48%) | 46% (52%) | 49% (57%) |
Note: IPv4 addresses were mapped to location using their ASN/BGP announcing network information, with IP-geolocation based mappings listed afterwards in brackets. Not every IPv4 address geolocates to a specific country at all points in time, hence the variation between the two data sets.
– Timely Response to Emerging Cyber Threats and Latest Vulnerabilities
Throughout 2024, our dynamic Shadowserver team continued to prove its ability to quickly respond to the latest, most significant cyber threats – thereby ensuring that our network remediation reports remained timely, relevant, and actionable. Within one to two days of the announcement of many of the most serious new vulnerabilities in Internet-facing devices, we effectively utilized our Global Honeypot Sensor Network to analyze new attack data, then used that information to enhance our Internet-wide scanning – ultimately enabling us to identify devices that are vulnerable and (when possible) compromised on networks around the world.
For each new vulnerability we acted on, we:
(1) provided advance notice to our Shadowserver Alliance partners and announced our findings on social media about the geographic location (by country or region) of each publicly exposed, vulnerable or compromised device;
(2) directly reported those vulnerable or compromised devices (by specific IP addresses) to our respective 9,000+ subscribing organizations and 201 National CSIRTs through our free, daily network remediation reports, so they could patch their networks before the threats were exploited (or further exploited) by threat actors; and
(3) utilized our free public Dashboard – funded by the UK FCDO and available at dashboard.shadowserver.org – to provide daily, aggregated, country-level statistics on a wide range of data sets about the number and location of publicly exposed, misconfigured, vulnerable or compromised devices detected on networks globally. This provides an independent resource for the media, public, and cyber policy makers to use to illustrate the size and scale of many emerging cybersecurity threats.
To keep up with all the latest insights, alerts, and information from Shadowserver, please join our public mailing list and follow us on social media:
2024 Operational Highlights
Some of the most significant cyber threats Shadowserver identified and shared daily with Internet defenders in 2024 included:
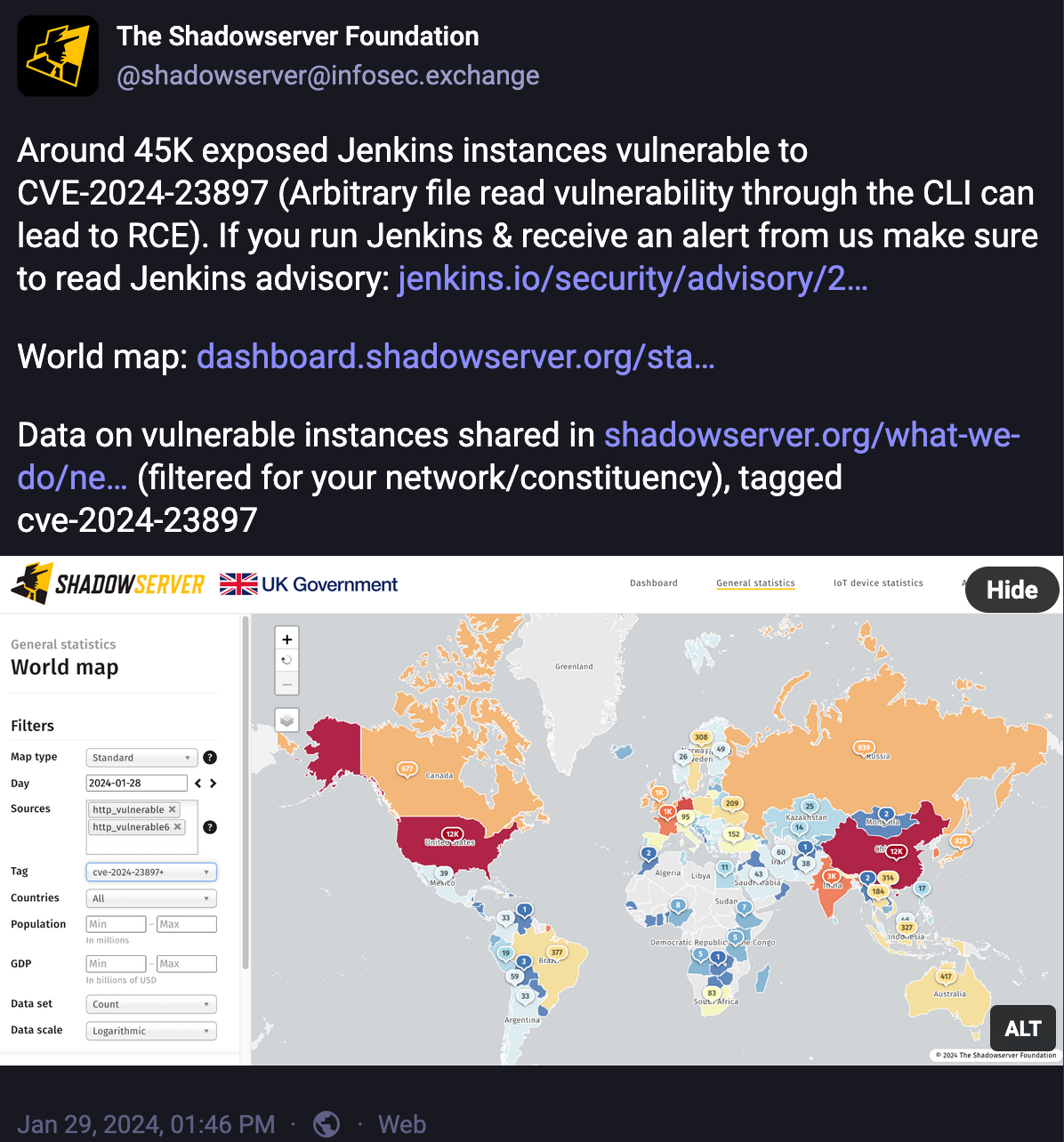
- In January, we identified around 45,000 publicly exposed Jenkins instances (a popular open source automation server) vulnerable to CVE-2024-23897 with a CVSS severity score of 9.8 rated CRITICAL. If exploited, this vulnerability would allow threat actors to gain unauthorized file access on the file system and possibly gain the ability to read entire files, thereby posing a significant risk to the integrity and confidentiality of sensitive information. [NOTE: CVE is an acronym for ‘Common Vulnerabilities and Exposures’ which is a public database of documented security flaws in computer hardware and software. CVSS is an acronym for ‘Common Vulnerability Scoring System’, a technical standard for assessing the severity of vulnerabilities in computer systems, with vulnerabilities scored on a scale from 1.0 to 10.0 and given a rating such as CRITICAL for the most serious vulnerabilities]
- In February, we improved our scanning for publicly exposed Ivanti Connect Secure VPNs (a popular corporate remote access solution) to better detect unpatched versions vulnerable to CVE-2024-22024 with a CVSS severity score of 8.3 rated HIGH (~3,900 identified) and CVE-2024-21887 with a CVSS severity score of 9.1 rated CRITICAL (~1,000 identified). Exploiting these vulnerabilities would allow a threat actor to access certain restricted information and resources without authentication.
- Also in February, we improved our scanning for publicly exposed ConnectWise ScreenConnect (a self hosted remote desktop application) to better detect instances vulnerable to CVE-2024-1709 with a CVSS severity score of 10.0 rated CRITICAL / CVE-2024-1708 with a CVSS severity score of 8.4 rated HIGH (~8,200 identified). If exploited, these vulnerabilities allow threat actors to gain full administrative control over the ScreenConnect instance and potentially upload malicious code onto the system.
- In March, we started sharing data on IP addresses vulnerable to a new type of Denial of Service attack – the “Loop DoS” attack – based on DNS, NTP and TFTP protocol scans in our new Loop DoS Report. Over 167,500 vulnerable instances were found on 2024-03-20. The application-layer loop DoS vulnerabilities were discovered by the security researchers Yepeng (Eric) Pan and Christian Rossow from the CISPA Helmholtz Center for Information Security in Germany.
- In April, we reported instances of Palo Alto Networks (PAN) GlobalProtect (which extends PAN’s next-gen firewall products to protect mobile workforces) vulnerable to CVE-2024-3400 with a CVSS severity score of 10.0 rated CRITICAL (6,634 identified). If exploited, this vulnerability allows threat actors to gain control over the system and remotely access sensitive information without authentication, steal data, install malware or otherwise disrupt network operations.
- Also in April, we reported instances of Qlik Sense (a data visualization and business intelligence tool) vulnerable to unauthenticated remote code execution CVE-2023-48365 with a CVSS score of 9.9 rated CRITICAL (2,894 identified), which were targeted and exploited by the Cactus ransomware group. Through collaboration with Fox-IT and DIVD in The Netherlands, 91 compromised devices were detected.
- In June, we reported instances of VMware vCenter (server management software that provides a centralized platform for controlling hypervisor environments and providing visibility across hybrid clouds) vulnerable to CVE-2024-37079 with a CVSS severity score of 9.8 rated CRITICAL and CVE-2024-37078 (1,200 identified). If exploited, these vulnerabilities allow threat actors to elevate privileges on the network and perform remote code execution.
- Also in June, very shortly after vulnerability details were first published, we reported seeing attempts against our honeypots to exploit popular Mass File Transfer (MFT) application Progress MOVEit Transfer via CVE-2024-5806 with a CVSS severity score of 9.8 rated CRITICAL. If exploited, this vulnerability allows threat actors to bypass authentication and possibly gain unauthorized access to the network, thereby leading to data access and the potential for further exploitation. Publicly exposed MOVEit instances had previously been targeted by the CL0P ransomware actors the previous year, with major impact.
- In July, we reported instances of GeoServer (an open source server for sharing geospatial data) vulnerable to CVE-2024-36401 with a CVSS severity score of 9.8 rated CRITICAL (6,635 identified). If exploited, this vulnerability allows threat actors to perform remote code execution and potentially run malicious code on the network.
- We also reported publicly exposed instances of VMware ESXi hypervisors (their most popular free bare metal hypervisor) potentially vulnerable to CVE-2024-37085 with a CVSS severity score of 7.2 rated HIGH (20,275 identified). This vulnerability was found to be exploited by several ransomware operators to obtain full administrative permissions on the hypervisors, allowing them to encrypt the file system and potentially exfiltrate data or move laterally within the network.
- In August, immediately after the U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced that SolarWinds Help Desk (a popular IT ticketing system) was being actively exploited in the wild using vulnerability CVE-2024-28986 with a CVSS severity score of 9.8 rated CRITICAL, we added scanning to identify publicly exposed instances, which we added to our daily reports (812 publicly exposed instances found on 2024-08-18). If exploited, this vulnerability allows threat actors to execute arbitrary code and potentially gain access to sensitive areas of the network. Once inside, they can move laterally within the network, posing substantial risk to data integrity and system security.
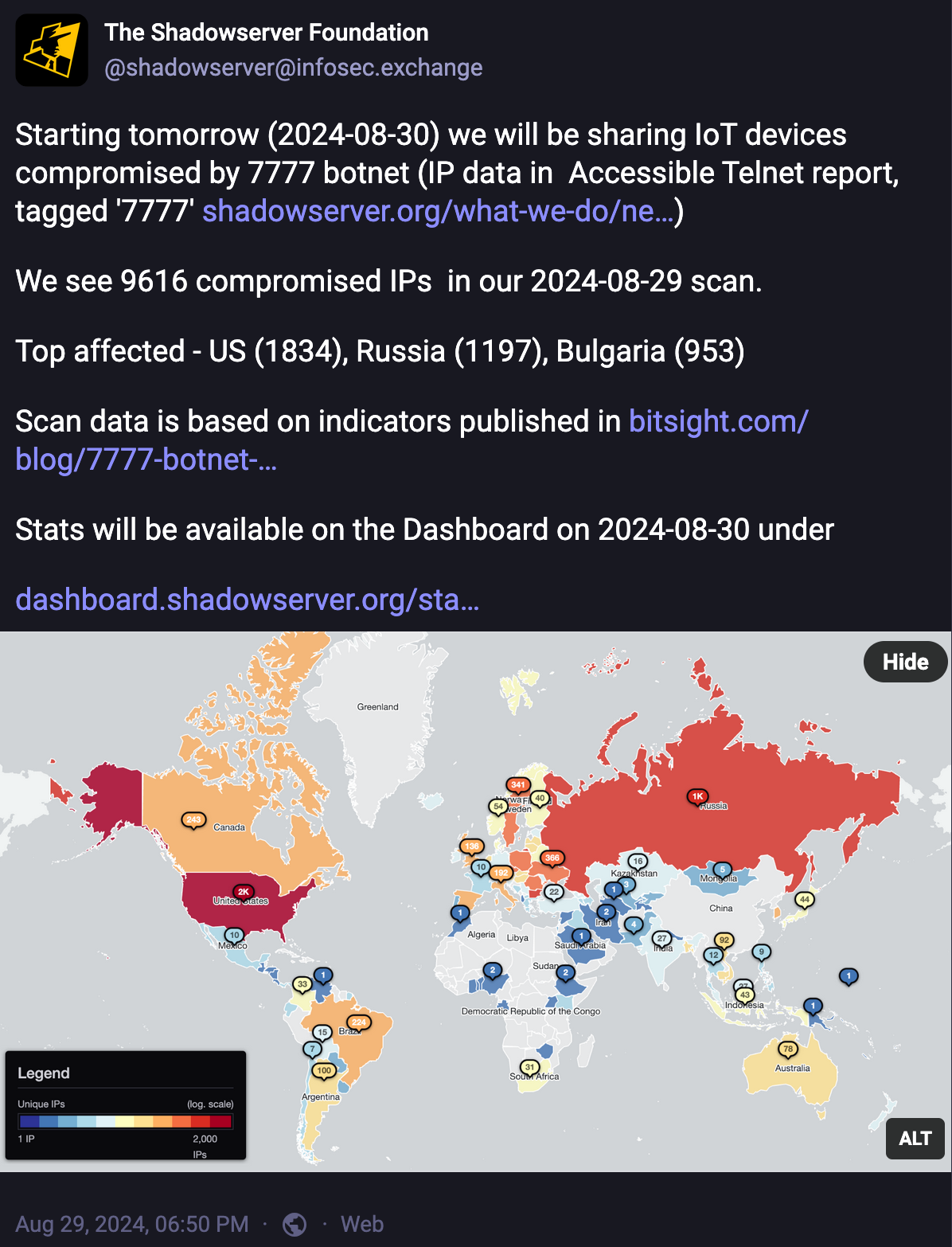
- Also in August, we reported Internet of Things (IoT) devices compromised by the 7777 botnet (9,616 detected). Also known as the “Quad7” botnet, the 7777 botnet is estimated to have compromised more than 175,000 IoT devices and is believed to be used primarily to conduct brute force attacks, guessing credentials to web applications and edge network devices to gain remote access.
- Also in August, CISA informed organizations about threat actors targeting improperly configured Cisco networking devices after observing them acquire system configuration files by abusing available protocols or software, such as the legacy Cisco Smart Install (SMI) feature. After CISA published its alert, we reported seeing over 6,000 IP addresses with the Cisco SMI feature publicly exposed to the Internet.
- In September, we detected Samsung Techwin Network Video Recorder Web Viewer devices compromised with a webshell (used by threat actors as a backdoor, with ~600 detected). This detection and data sharing was made possible thanks to successful collaboration with the Kingdom of Saudi Arabia’s National Cybersecurity Authority (KSA NCA).
- Also in September, we added a new Compromised IoT Report that aggregates information about compromised IoT devices detected through other means than HTTP-based scan detection. This includes a number of new sources, including our collaboration with an external partner to detect compromised SSH hosts by identifying malicious known public keys installed by attackers, as well as identification of compromised devices through correlation of our scan and Global Honeypot Sensor Network findings.
- In October, we reported the IP addresses of Fortinet FortiOS devices (the unified security platform for security vendor Fortinet’s network devices) likely vulnerable to CVE-2024-23113 with a CVSS severity score of 9.8 rated CRITICAL (87,390 identified). If exploited, this vulnerability allows a threat actor to remotely execute arbitrary code or commands on a system.
- Also in October, we issued an urgent Special Report identifying Fortinet FortiManager devices targeted / compromised using vulnerability CVE-2024-47575 with CVSS severity score of 9.8 rated CRITICAL. By sending specially crafted messages, threat actors can gain control of the FortiManager devices and execute arbitrary commands. The vulnerability can also allow threat actors to exfiltrate sensitive data, including hashed passwords, from managed FortiGate devices, increasing the risk of lateral movement and broader network breaches.
- In November, we reported that our Global Honeypot Sensor Network had detected a zero-day exploit being used in the wild to target End of Life (EOL) GeoVision Network Video Devices. We collaborated with the Taiwanese National CSIRT TWCERT/CC and device vendor GeoVision to confirm the zero-day vulnerability that allowed unauthenticated attackers to inject arbitrary commands and have CVE-2024-11120 assigned, with a CVSS score of 9.8 rated CRITICAL. The vulnerability was exploited by a Mirai botnet variant and Shadowserver was credited with the discovery.
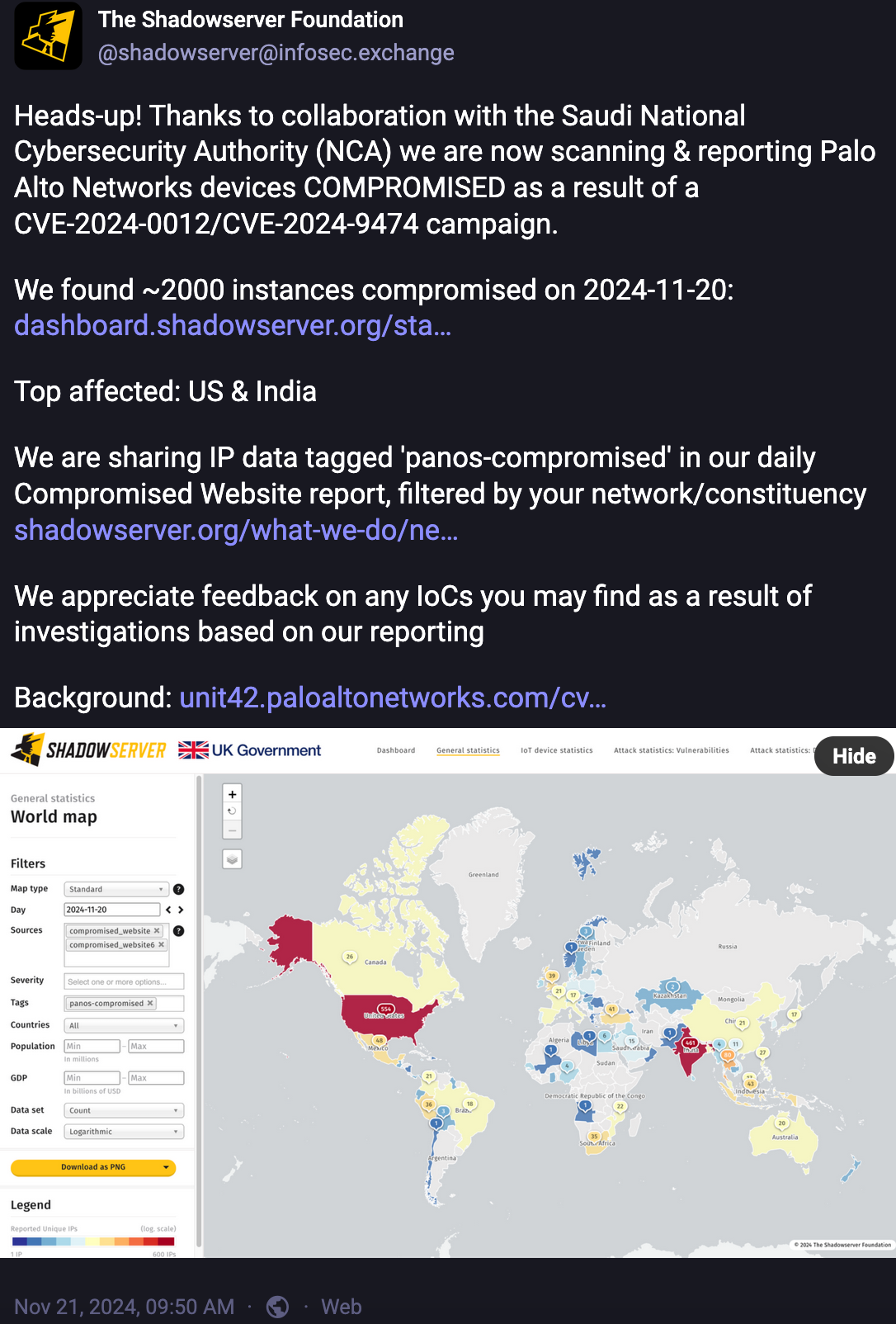
- Also in November, we reported Palo Alto Networks (PAN) devices vulnerable to CVE-2024-0012 with a CVSS severity score of 9.8 rated CRITICAL (~2,700 detected). If exploited, this vulnerability allows a threat actor to bypass authentication and gain administrator privileges to the network, and to potentially tamper with the configuration or exploit other vulnerabilities. We thanked watchTowr, a new Shadowserver Alliance partner for 2024, for sharing their insights that enabled our scans. This highlighted yet another example of the value of the Shadowserver Alliance, where like-minded organizations like watchTowr join Shadowserver and other Alliance partners to collaborate in a community where information is regularly shared for the benefit of each other and the public.
- Thanks to information provided by the Kingdom of Saudi Arabia’s National Cybersecurity Authority (KSA NCA), we were then able to report PAN devices compromised using CVE-2024-0012 / CVE-2024-9474. The cyber threat intelligence sharing contribution of the KSA NCA is just one of many examples that highlight the value of Shadowserver’s trusted partnerships with National CSIRTs, Shadowserver Alliance partner organizations, security researchers, and others willing to consistently share information for the benefit of the global community.
- In December, we reported publicly exposed instances of another popular Mass File Transfer (MFT) application Cleo Harmony/VLTrader/LexiCom that were vulnerable to CVE-2024-50623 with a CVSS severity score of 9.8 rated CRITICAL, which was added to CISA’s Known Exploited Vulnerability catalog (930 identified). If exploited, this vulnerability can allow threat actors to remotely execute code on the system and was likely used by ransomware threat actors CL0P in their most recent round of data breaches and victim extortion.
- Also in December, the US Cybersecurity and Infrastructure Security Agency (CISA) and the US Office of the National Cyber Director (ONCD) published their “Playbook for Strengthening Cybersecurity in Federal Grant Programs for Critical Infrastructure”. The guide is designed to enable grant-making agencies to incorporate cybersecurity into their grant programs, and to enable grant recipients to build cyber resilience into their grant-funded infrastructure projects. The guide includes a comprehensive list of cybersecurity resources available to support grant recipient project execution. Shadowserver is included in the Advisory Support / Technical Assistance Service section in the Protect category. [Note: the content of whitehouse.gov was updated after the January 2025 change of US Administration, but the archived content can still be found at the Biden Adminstration archive.]

- Finally, we were proud to be recognized by leading vulnerability intelligence vendor VulnCheck as the “Earliest Reporter of Exploitation in the Wild” in 2024. Using our extensive Global Honeypot Sensor Network, our Shadowserver team of experts led the way in timely identifying and reporting when vulnerabilities were being actively exploited in the wild by threat actors. As VulnCheck’s Patrick Garrity noted, “The public disclosure of known exploited vulnerabilities provides the security community with critical insights into real-world threats that are often immediately actionable”.

Shadowserver’s Global Cybersecurity Capacity Building
Shadowserver expanded its Global Cybersecurity Capacity Building (CCB) efforts in 2024, due in significant part to the support and forward-thinking approach of the United Kingdom’s Foreign Commonwealth and Development Office (UK FCDO) – a global leader within the cybersecurity capacity building ecosystem.
Beginning in 2021 and continuing to the present day, the UK FCDO and Shadowserver have partnered on extensive global cybersecurity capacity building efforts in Africa, the Indo-Pacific, Central and Eastern Europe, and the Gulf Region of the Middle East.
These efforts have included a multifaceted approach that combines providing free cyber threat intelligence, outreach to National CSIRTs and network owners, expert analysis of the threat landscape, technical assistance, training, and collaboration opportunities. The goals of these initiatives are to provide National CSIRTs, government agencies, network operators and system defenders in a target country or region with the necessary knowledge, skills, and tools to improve threat detection; enable effective incident response; and strengthen cyber resilience.
A critically important component of any cybersecurity capacity building effort is the ability to track and assess performance, monitor progress, and measure success. Our extensive data collection capabilities, combined with our advanced technical expertise, allow us to measure publicly exposed attack surfaces by detecting misconfigured, vulnerable, and compromised devices on networks within a country or a region. Using our data, we can then monitor progress in patching and remediation efforts to measure improvements in the security of those networks. The progress can be tracked over time and viewed in aggregated country-level statistics on our FCDO-funded public Dashboard, which can be accessed at dashboard.shadowserver.org.
The first half of 2024 saw the FCDO-funded addition of another 69 languages, which when combined with the existing 6 languages, means that professionally translated localized content is now available on our public Dashboard for the majority of the commonly spoken languages worldwide – including left to right and right to left character sets – representing another great step in international usability (click the language button in the bottom right corner to try it out).
2024 marked a new milestone in the UK FCDO / Shadowserver cybersecurity capacity building partnership. Building off the success of the partnership’s efforts in the preceding years and utilizing the UK Integrated Security Fund (ISF), the FCDO committed to:
- funding Shadowserver’s Core Mission public benefit services through March 2025;
- funding our 3-year cybersecurity capacity building projects in Africa and the Indo-Pacific through March 2027. Our current three-year project includes funding to hire two new Shadowserver team members who have assumed the roles of Regional Coordinators/Liaisons to Africa and the Indo-Pacific, respectively, and each will reside within their focus region; and
- continuing funding our ongoing capacity building efforts in the Middle East’s Gulf Region through March 2025.
Our Shadowserver team took on numerous additional cybersecurity capacity building projects in 2024, including:
- As part of an effort that spanned several months of 2024, Shadowserver partnered with fellow nonprofit organizations The Hague Humanity Hub, the CyberPeace Institute, and the Connect2 Trust Foundation in a project titled ‘Cyber Resilience for NGOs’ (CR4NGO consortium), funded by the Dutch Government’s Digital Trust Center. The purpose of the project was to increase the cyber resilience of non-governmental organizations (NGOs), since NGOs are frequently targeted by cyber attacks but lack the resources and expertise to adequately protect themselves. The project’s objectives were to: map the cyber threat landscape of NGOs; clarify the human impact of cyber attacks and the effect not only on the NGOs but also the beneficiaries they serve; and provide customized information about cyber threats to help NGOs better protect themselves. The project culminated in the December release of a report that contained data and analysis contributed by Shadowserver, ‘Cyber Resilience for NGOs: A Collective Intelligence Effort Threat Landscape Report’, available in English and Dutch.
 In February, we participated in the joint UK-France led Pall Mall Process event in London to tackle the proliferation and misuse of commercial cyber intrusion tools. At the event, UK Deputy Prime Minister Oliver Dowden gave the keynote address in which he announced the UK Government’s pledge of £1 million to Shadowserver to “help them expand the access they provide to early warning systems, and to cyber resilience support for those impacted by cyber-attacks”. [Note: This pledge of £1 million was subsequently extended via the larger FCDO/UK ISF funding commitment to Shadowserver discussed above.]
In February, we participated in the joint UK-France led Pall Mall Process event in London to tackle the proliferation and misuse of commercial cyber intrusion tools. At the event, UK Deputy Prime Minister Oliver Dowden gave the keynote address in which he announced the UK Government’s pledge of £1 million to Shadowserver to “help them expand the access they provide to early warning systems, and to cyber resilience support for those impacted by cyber-attacks”. [Note: This pledge of £1 million was subsequently extended via the larger FCDO/UK ISF funding commitment to Shadowserver discussed above.]- This resulted in additional post-exploitation frameworks (stolen or cracked copies of ‘red team’ tools used for legitimate penetration testing that are abused by threat actors to enable system intrusions and lateral movement in victim networks) being added to our scan-based tracking, with daily statistics about 40+ tracked frameworks being made available via our public Dashboard, and detailed data being shared with National CSIRTs via our Post-Exploitation Framework Report.
- We continued to participate in the Pall Mall Process throughout 2024 and into 2025. We are named in the Pall Mall Process Consultation on Good Practices Report and listed as a participant in the ‘Civil society and academia represented’ section.
- Also in February, Shadowserver’s Industry Relationship Manager Jonathan Flaherty was in Bangkok, Thailand where, with the support of the UK FCDO, he met with members of Thailand’s National Cyber Security Agency (NCSA.TH), to include Air Chief Marshal Amorn Chomchoy (Secretary-General of the National Cyber Security Committee, and Air Chief Marshal Chaded Kuhakongkit, Assistant Secretary-General). The meeting included discussions on cybersecurity capacity building, effective use of Shadowserver’s network remediation reports, training opportunities, and the country’s threat landscape.

- In October, Shadowserver’s Industry Relations Manager Jonathan Flaherty led a training segment on effective use of Shadowserver’s free cyber threat intelligence at the TrustBroker Africa’s SIM3 Auditor Certification Training in Cotonou, Benin.

- In November, Shadowserver’s CEO Piotr Kijewski led a full-day training titled ‘Getting the Most Out of Free Shadowserver Daily Feeds & Other Community Services via Automation’ at the FIRST & AfricaCERT Symposium for the African and Arab Regions in Livingstone, Zambia in collaboration with Lawrence Muchilwa from FIRST.org.

- In December, the UK Government published its 2023 – 2024 annual report on the Conflict, Stability and Security Fund (CSSF) (which was the precursor to the UK’s current Integrated Security Fund (ISF)). The section on ‘Transnational Threats: Cyber’ highlighted our project work funded through the CSSF Indo-Pacific Cyber Programme – ‘Improving Threat Data for Indonesia, Malaysia, the Philippines, and Thailand’ saying “This project improved the quality of free daily cyber threat intelligence provided to national telecoms and cyber security incident response teams. In early 2024, a significant and new malware vulnerability was identified in the region, released by a Chinese state actor. Shadowserver quickly responded by detecting and reporting on the exposed networks and devices, alerting cyber response teams, network owners and media. New scanning techniques were developed to determine whether exposed devices were vulnerable and reported through existing mechanisms. Through CSSF funding, Shadowserver helped multiple governments and users in the Indo-Pacific and across the world, including the UK, to help identify and reduce vulnerabilities to a new cyber threat”.
- Throughout most of the year we also worked to support Pacific Island CSIRTs thanks to funding from New Zealand’s National CSIRT CERT NZ.
Shadowserver’s Free Support to Law Enforcement in the Fight Against Cybercrime
Shadowserver’s free support to some of the world’s most significant Law Enforcement disruption operations was as prevalent in 2024 as at any point in our 20-year history. As long-time trusted partners of Law Enforcement Agencies around the world, we provide valuable, free, timely technical assistance and expertise to Law Enforcement at no cost to their taxpayers.
Shadowserver’s support included: sinkholing services (in which threat actors’ control over infected victim computers is severed and botnet traffic is redirected to sinkhole servers operated by Law Enforcement or Shadowserver, typically pursuant to a lawful court order); quarantining malicious domains (used by threat actors to facilitate their crimes) using the Registrar of Last Resort (RoLR), Shadowserver’s sister nonprofit organization and ICANN-accredited special purpose DNS registrar; and using Shadowserver’s existing daily network remediation report channels to effectively deliver free victim notifications to 9,000 subscribing organizations and 201 National CSIRTs covering 176 countries around the world.
Highlights from Shadowserver’s 2024 support to Law Enforcement included:
- In February, the U.S Department of Justice cited the valuable assistance provided by Shadowserver and its partners when it announced Operation Dying Ember, a court-authorized disruption of the Moobot malware botnet controlled by the Russian Federation’s Main Intelligence Directorate of the General Staff (GRU). The botnet was made up of hundreds of small office / home office (SOHO) routers that GRU Military Unit 26165 used to conceal and enable a variety of crimes against targets of interest to the Russian government, including U.S. and international governments and military, security, and corporate organizations.
 In June, FBI Cyber Assistant Director Bryan Vorndran’s keynote address at the 2024 Boston Conference on Cybersecurity included the following remarks about Shadowserver’s support of Operation Dying Ember: “This was an operation we could not have accomplished without corporate partners, particularly Microsoft and the Shadowserver Foundation” (image provided by the FBI).
In June, FBI Cyber Assistant Director Bryan Vorndran’s keynote address at the 2024 Boston Conference on Cybersecurity included the following remarks about Shadowserver’s support of Operation Dying Ember: “This was an operation we could not have accomplished without corporate partners, particularly Microsoft and the Shadowserver Foundation” (image provided by the FBI).- In April, the UK’s Metropolitan Police and Europol announced a multi-agency Law Enforcement operation dubbed Operation PhishOFF, supported by Shadowserver and other private sector partners, that disrupted the LabHost crime group who operated a phishing-as-a-service platform for cybercriminals and online fraudsters. The LabHost platform was successfully shut down, 37 suspects were arrested, and 70 locations were searched. Operation PhishOFF ultimately won the prestigious Europol Excellence Award for ‘Innovation for an Operation’.
- In May, Shadowserver was recognized, alongside its partners, by the U.S. Department of Justice for supporting the FBI-led investigation Operation Tunnel Rat, that led to the dismantling of the 911 S5 residential proxy service botnet and the arrest of the botnet’s administrator. According to U.S. Attorney General Merrick Garland, the botnet “facilitated cyber attacks, large-scale fraud, child exploitation, harassment, bomb threats, and export violations”. FBI Director Christopher Wray noted that the botnet was “likely the world’s largest botnet ever” associated with “more than 19 million unique IP addresses” in 200 countries. Shadowserver announced that it was reporting current 911 S5 proxy botnet infections in its daily sinkhole reports, to notify subscribing organizations and National CSIRTs about infected devices in their networks in need of remediation.

- Also announced in May, Shadowserver assisted in an international, multi-agency Law Enforcement operation called Operation Endgame, which was also nominated as one of three finalists for the prestigious Europol Excellence Award for ‘Innovation for an Operation’. Coordinated by Europol and led by Law Enforcement in France, Germany, the Netherlands, Denmark, the United States and the United Kingdom, Operation Endgame was the largest-ever operation against loader/dropper botnets, which play a significant role in the deployment of other malware such as ransomware. The operations targeted dropper and loader malware variants, including IcedID, SystemBC, Pikabot, Smokeloader, Bumblebee, and Trickbot. As a result of the victim data collected by Law Enforcement and shared with Shadowserver, Shadowserver issued multiple Special Reports for its subscribing organizations and National CSIRTs containing information about IP addresses and computer systems believed to have been infected with IcedID/Latrodectus malware and SystemBC malware.
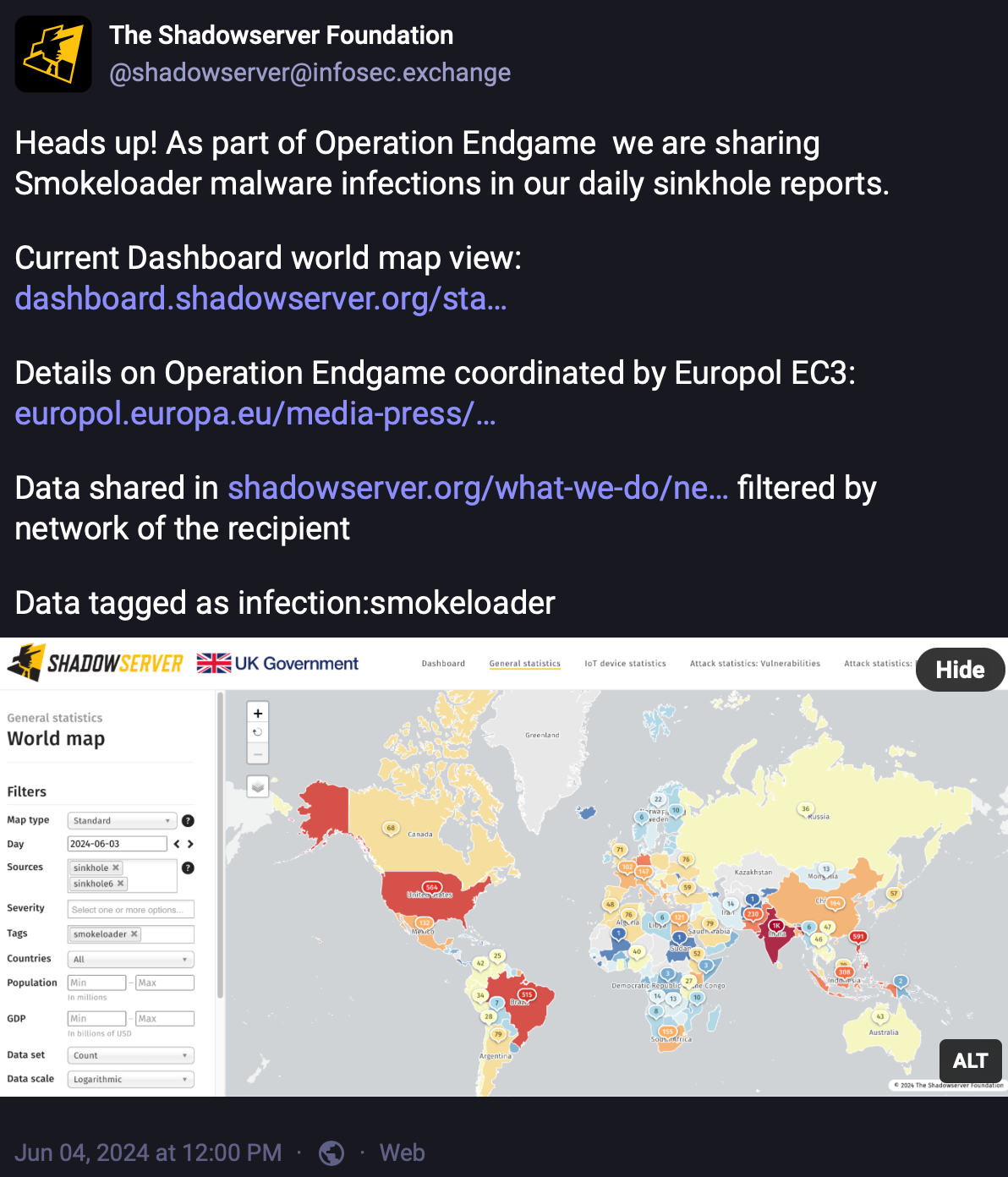
- Our work with partners in Operation Endgame on custom sinkholes also enabled Shadowserver to report Smokeloader malware infections in its daily sinkhole event reports, to help effectuate the cleaning of victims’ devices from dropped secondary infections, while also enabling reporting of aggregated country-level statistics on the Shadowserver public Dashboard to help raise awareness.
- In July, the UK’s National Crime Agency (NCA) and Europol announced Operation MORPHEUS, a coordinated global Law Enforcement action against illicit pirated and unlicensed versions of Fortra Cobalt Strike software (a legitimate commercial penetration testing tool designed to help security experts identify vulnerabilities in networks to help improve cybersecurity). The illicit Cobalt Strike versions had been used by threat actors for more than a decade as a post-exploitation framework to infiltrate victims’ networks and conduct attacks. The operation involved cooperation between Law Enforcement and the private sector, including Shadowserver, who supplied LE partners with Cobalt Strike Beacon data. As the Europol press release stated, “Cooperation with the private sector was instrumental in the success of this disruptive action. A number of private industry partners supported the action, including BAE Systems Digital Intelligence, Trellix, Spamhaus, abuse.ch, and The Shadowserver Foundation”.
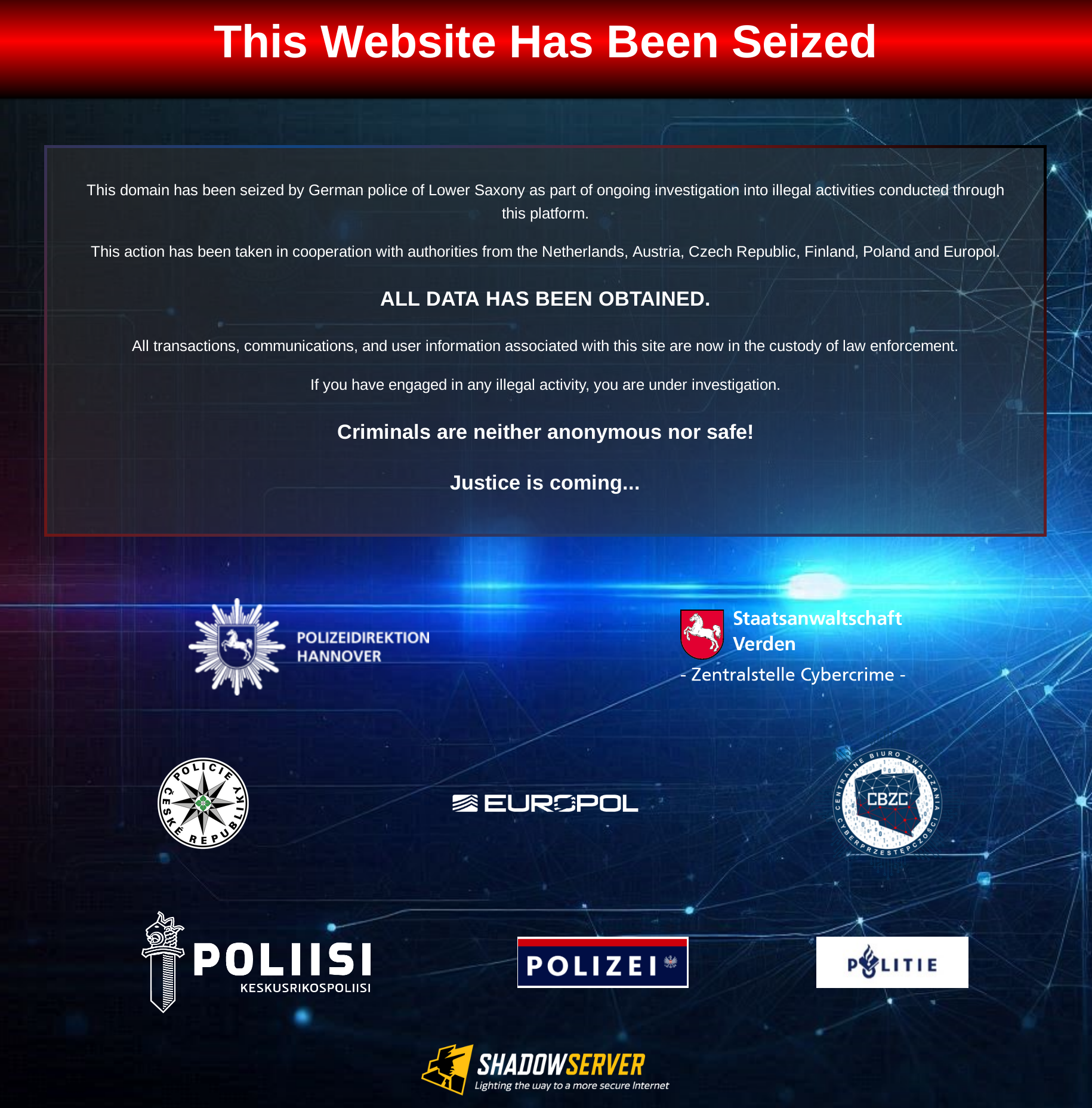
- In December, Law Enforcement Agencies announced a coordinated international operation that dismantled key structures of a sophisticated criminal network responsible for facilitating large-scale online fraud. Led by the Verden Public Prosecutor’s Office and Hanover Police Directorate of Lower Saxony (Germany), with support from Europol and police agencies from the Netherlands, Finland, Austria, Czech Republic, Poland, and Norway, the operation successfully shut down over 50 servers, secured extensive digital evidence, and led to the pretrial detention of two criminal suspects.
- Throughout 2024, Shadowserver continued work on the European Union Internal Security Fund (ISF) financed MISP-LEA project, a joint collaboration with Computer Incident Response Center Luxembourg (CIRCL) to operate a dedicated free Malware Information Sharing Platform (MISP) instance for the Law Enforcement Agency (LEA) community in the EU (but also with involvement of LEAs worldwide). Shadowserver feeds the MISP instance with cybercrime relevant threat intelligence focused on the needs of LEAs. The Shadowserver data feeds were expanded throughout the year.
 In December, Shadowserver’s Tod Eberle presented at two cybercrime disruption workshops held in The Hague, Netherlands. Tod’s presentation included an explanation of Shadowserver’s free technical support available to Law Enforcement in their cybercrime investigation and disruption operations, as well as Shadowserver’s contributions to the 911 S5 proxy botnet disruption led by the DOJ, Federal Bureau of Investigation (FBI), the Defense Criminal Investigative Service (DCIS), and many international partners. The first event was hosted by the United States Department of Justice (US DOJ) and its Office of Overseas Prosecutorial Development, Assistance and Training (OPDAT). Attendees included the DOJ’s International Computer Hacking and Intellectual Property (ICHIP) advisors from four regions — Africa, Eastern Europe, Latin America, and Southeast Asia — who each accompanied expert cybercrime prosecutors and investigators from the countries within their respective regions, to include Ghana, Kenya, Nigeria, Croatia, Poland, Romania, Argentina, Brazil, Costa Rica, Malaysia, Philippines, Singapore and Thailand. The second event was co-hosted by the US DOJ and Eurojust, and attendees included prosecutors and judicial authorities from Eurojust member countries, as well as representatives of the European Judicial Cybercrime Network.
In December, Shadowserver’s Tod Eberle presented at two cybercrime disruption workshops held in The Hague, Netherlands. Tod’s presentation included an explanation of Shadowserver’s free technical support available to Law Enforcement in their cybercrime investigation and disruption operations, as well as Shadowserver’s contributions to the 911 S5 proxy botnet disruption led by the DOJ, Federal Bureau of Investigation (FBI), the Defense Criminal Investigative Service (DCIS), and many international partners. The first event was hosted by the United States Department of Justice (US DOJ) and its Office of Overseas Prosecutorial Development, Assistance and Training (OPDAT). Attendees included the DOJ’s International Computer Hacking and Intellectual Property (ICHIP) advisors from four regions — Africa, Eastern Europe, Latin America, and Southeast Asia — who each accompanied expert cybercrime prosecutors and investigators from the countries within their respective regions, to include Ghana, Kenya, Nigeria, Croatia, Poland, Romania, Argentina, Brazil, Costa Rica, Malaysia, Philippines, Singapore and Thailand. The second event was co-hosted by the US DOJ and Eurojust, and attendees included prosecutors and judicial authorities from Eurojust member countries, as well as representatives of the European Judicial Cybercrime Network.
The Shadowserver Alliance
The Shadowserver Alliance continued to grow in 2024 with the addition of many new partner organizations. The Alliance is made up of like-minded organizations that support Shadowserver’s nonprofit mission while enjoying the many benefits the Alliance has to offer. Among other things, the Alliance provides partners with access to a community of cybersecurity experts (led by Shadowserver team members) that offers timely insights and information on the latest vulnerabilities, attack observations, and other significant cyber threats that organizations need to stay ahead of to ensure their networks are secure. 2024 saw a number of organizations become new Alliance partners, including: The Digital Trust Center (DTC) of the Netherlands, EURid, Nihon Cyber Defence, Team Cymru, Trivest AG, and watchTowr. The complete list of Alliance partners can be found on our Alliance Partner page.
Cybersecurity Community Initiatives and Conference Presentations
Throughout 2024, Shadowserver continued to be engaged in the Common Good Cyber initiative (a global initiative with the goal of identifying and implementing innovative models for sustaining groups, organizations, and individuals involved in critical cybersecurity functions for the broader Internet community) along with other prominent cybersecurity nonprofits. This included participating in the opening panel of the first Common Good Cyber Workshop 2024 in Washington DC in February, as well as during the follow up Beyond125 workshop in The Hague in October.
We also continually engaged in Craig Newmark’s Cyber Civil Defense and PauseTake9 efforts.
Shadowserver continued to be one of the few ‘exploitation in the wild’ data contributors to the Forum for Incident Response and Security Teams (FIRST)’s Exploit Prediction Scoring System (EPSS), a data-driven industry standard for estimating the likelihood (probability) that a software vulnerability is being exploited in the wild, which is being adopted worldwide, as well as being a recurring contributor to the Verizon 2024 Data Breach Investigations Report (DBIR).
We also presented at dozens of cybersecurity events worldwide, including the FIRST.org Annual Conference in Japan, National CSIRT events such the AUSCERT 2024, CERT.BR Brazilian CSIRTs forum, NCSC.NL One Conference, as well as many closed door LEA and government events.
You can read our detailed background on Shadowserver’s work in this Help Net Security interview by CEO Piotr Kijewski, as well as on our financial challenges in this Common Good Cyber interview.
You can also visit our new Shadowserver Youtube channel!
Thank You to Our Supporters
As a nonprofit organization, we survived in 2024 through the generous support of the United Kingdom’s Foreign, Commonwealth and Development Office (UK FCDO), Craig Newmark of Craig Newmark Philanthropies, our Shadowserver Alliance partners, and those who supported us through donations, voluntary invoicing, and funded projects. To all of you, the entire Shadowserver team extends a sincere and heartfelt thank you.
We close by once again thanking all of our supporters who helped make 2024 a resounding success – the National CSIRT community; our trusted Law Enforcement partners from around the globe; our financial supporters; and those who shared with us data, intelligence, and insights that helped make our services more timely, relevant, and effective. Without your support, we would not be able to provide free public benefit services that help secure networks and raise the baseline of cybersecurity worldwide.
How You Can Help Support Shadowserver (to Support You and the Community)
The complex technical nature and global scale of our free public benefit services mean that we must operate our own data center and maintain a small but highly skilled staff, resulting in operating costs totaling approximately $5 million per year at a minimum. Less than 1% of entities subscribed to our free daily network reports currently choose to support us financially. Achieving consistent, sustainable funding is a constant and significant challenge.
To continue providing free public benefit services that help make the Internet more secure for all, we need your support! Please consider joining the Shadowserver Alliance, or supporting us with a one-time donation, a request for a voluntary invoice, or a funded project by contacting us, and visiting our Partners Page for more information.