Update 2025-12-16
A second Rhadamanthys Historical Bot Infections Special Report has been run dated 2025-12-05. This covered the same time period as the original Special Report, but contained an expanded set of victim data, so please check if you received any additional notifications for remediation.
The second Special Report included additional datasets obtained from seized criminal infrastructure that were not available at the time the first Special Report was run (on 2025-11-12). This enhanced second Special Report included 91,937,512 different information stealing events recorded on victim computers (+5,722,588 compared with the first Special Report), corresponding to 567,215 (+41,912) unique IP addresses located in 18,276 (+602) different Autonomous Systems (ASNs), across 228 (+2) different countries.
Note: Due to a technical issue that potentially impacted some large report file downloads, this second Special Report was initially run on 2025-12-02 but re-run again on 2025-12-15. The 2025-12-15 Special Report contains the same data as the 2025-12-02 Special Report, but was resent again in case downloads of the original second Special Report were not 100% successful for all recipients. The statistics and images in this blog post were also updated on 2025-12-16 to take into account the enhanced (2025-12-02/2025-12-15) data sets, and the second Special Report was announced publicly.
Operation Endgame Season 1.0
On May 30th 2024, international Law Enforcement Agencies (LEAs) led by France, Germany and the Netherlands, and supported by Europol, Eurojust, Denmark, the United Kingdom, the United States, Armenia, Bulgaria, Lithuania, Portugal, Romania, Switzerland, Ukraine, and multiple private sector supporting partners, including The Shadowserver Foundation, jointly announced Operation Endgame. This was a groundbreaking collaborative effort to simultaneously disrupt many of the main malware dropper/loader families, which load additional secondary malware onto victim computers and were/are an essential primary enablers in the cybercrime ecosystem. Targets successfully disrupted included IcedID, SystemBC, Pikabot, Smokeloader and Bumblebee. Data from seized criminal backends was shared with Shadowserver, to distribute to 201 National CSIRTs in 175 countries and over 10,000 network owners globally, to aid in victim identification and remediation. As part of those efforts, multiple one-off Shadowserver Special Reports were run sharing large amounts of historical victim data, including for IcedID/Latrodectus and SystemBC, as well as live sinkholing and remote disinfection being performed for Smokeloader (and earlier disruption of Qakbot). The Operation Endgame official website launched, featuring a series of “Season 1” short videos about some of the threat actors behind these botnets, and their affiliate customers.
Operation Endgame Season 2.0
On May 23rd 2025, Operation Endgame 2.0 was announced, this time targeting information stealing malware (infostealers) as well as additional dropper/loader malware families. Targets included Bumblebee, Lactrodectus, Qakbot, Hijackloader, DanaBot, Trickbot, Warmcookie, and Endgame-aligned Lumma. Once again, multiple one-off Shadowsever Special Reports were run, including for IcedID/Latrodectus and Qakbot, and the Operation Endgame website was updated with a “Season 2” second series of short videos about the additional threat actors. Several individuals were added to the EU’s Most Wanted list and the Qakbot admins were indicted by the US Department of Justice.
Operation Endgame Season 3.0
On November 13th 2025, Operation Endgame 3.0 was announced. Coordinated by Europol and Eurojust, this is a joint effort between law enforcement and judicial authorities of Australia, Belgium, Canada, Denmark, France, Germany, Greece, Lithuania, the Netherlands, the United Kingdom and the United States, and over 30 supporting national and private sector partners, including Shadowserver, targeting additional cybercriminal ecosystem enablers. This included the notorious Rhadamanthys infostealer, which had grown to become one of the leading infostealers since Operation Endgame “Season 2” disrupted the infostealer landscape. Data seized by Law Enforcement in Operation Endgame “Season 3” is once again being shared through Shadowserver’s free daily Network Reports, to distribute to nCSIRTs and network owners, with the goal of quickly identifying and remediating victims. The Operation Endgame official website has been updated with a new “Season 3” short video entitled S03E01 “STICKY FINGERS”, about the Rhadamanthys infostealer.
The first output from these latest Operation Endgame “Season 3” activities is our new Rhadamanthys Historical Bot Infections Special Report, which provides notifications about devices infected with the Rhadamanthys infostealer malware between 2025-03-14 and 2025-11-11, including details about the large number of URLs and associated credentials stolen by the threat actor operating Rhadamanthys and their affiliates/customers.
- 201 National CSIRTs in 175 countries will receive a one-off Special Report about historical Rhadamanthys infected devices in their country, containing victim IP addresses and supporting meta data to allow system identification, filtered by geographical region.
- 10,000+ Network owners globally will receive a one-off Special Report about historical Rhadamanthys infected devices in their own networks of responsibility, containing victim IP addresses and supporting meta data to allow system identification.
This Rhadamanthys Historical Bot Infections Special Report was disseminated overnight on November 12th 2025 (with a second, expanded Special Report being run on 2025-12-02 and 2025-12-15). If you receive a Rhadamanthys notification, please act to identify and remediate those compromised devices and user accounts immediately. More information about the data contained in this Special Report can be found here.
General information about the Rhadamanthys infostealer malware can be found in Malpedia, which includes articles with links to remediation information. You can also check your email addresses in HaveIBeenPwned and the Dutch Police’s CheckYourHack site.
Anyone who has not yet signed up for Shadowserver’s free daily network reports can subscribe and register their network space here. If you sign up after the dissemination date, you can request a backdated Rhadamanthys Historical Bot Infections Special Report for your network (or country, for new nCSIRTs).
This reporting is provided in partnership with our international Law Enforcement partners, at no cost, as a public benefit service, and is part of Shadowserver’s mission to make the Internet more secure for all users.
Secondary Malware Infections
It is important to note that Rhadamanthys may have been used to drop additional malware on infected systems, so other malware infections may also be active on these systems and require further local remediation efforts. These victim systems may also have been used in historic or recent intrusions and ransomware incidents. We therefore ask all recipients of these Special Report notifications to not just consider Rhadamanthys in their incident response activities, but also the possibility of secondary infections and/or indication of wider lateral movement.
If you have received a Rhadamanthys Historical Bot Infections Special Report and you need more information about a specific infection, please contact us, and we can provide more details or put you in touch with the Law Enforcement investigating officers if required.
It should be noted that some IP addresses can be associated with multiple Rhadamanthys infections over that time period. A subset of the recorded Rhadamanthys “victims” are likely to actually be security researchers or sandbox systems, but these events have been included for completeness (hopefully, those people know who they are, and what they have been doing).
Rhadamanthys Historical Bot Infections – Data Analysis
The data shared in our Rhadamanthys Historical Bot Infections Special Report covers malware infections from the period from 2025-03-14 to 2025-11-11. We are publicly sharing some initial high level analysis of this Rhadamanthys historical bot infections dataset:
- The first dataset dated 2025-11-12 represented 86,214,924 different information stealing events recorded on victim computers, corresponding to 525,303 unique IP addresses located in 17,674 different Autonomous Systems (ASNs), across 226 different countries (so essentially the entire world). For each of the images below you can click on it to view a higher resolution version.
- The second enhanced dataset dated 2025-12-02 and 2025-12-15 included 91,937,512 different information stealing events recorded on victim computers (+5,722,588 compared with the first Special Report), corresponding to 567,215 (+41,912) unique IP addresses located in 18,276 (+602) different Autonomous Systems (ASNs), across 228 (+2) different countries.
For each of the images inline, you can click it to view a higher resolution version.
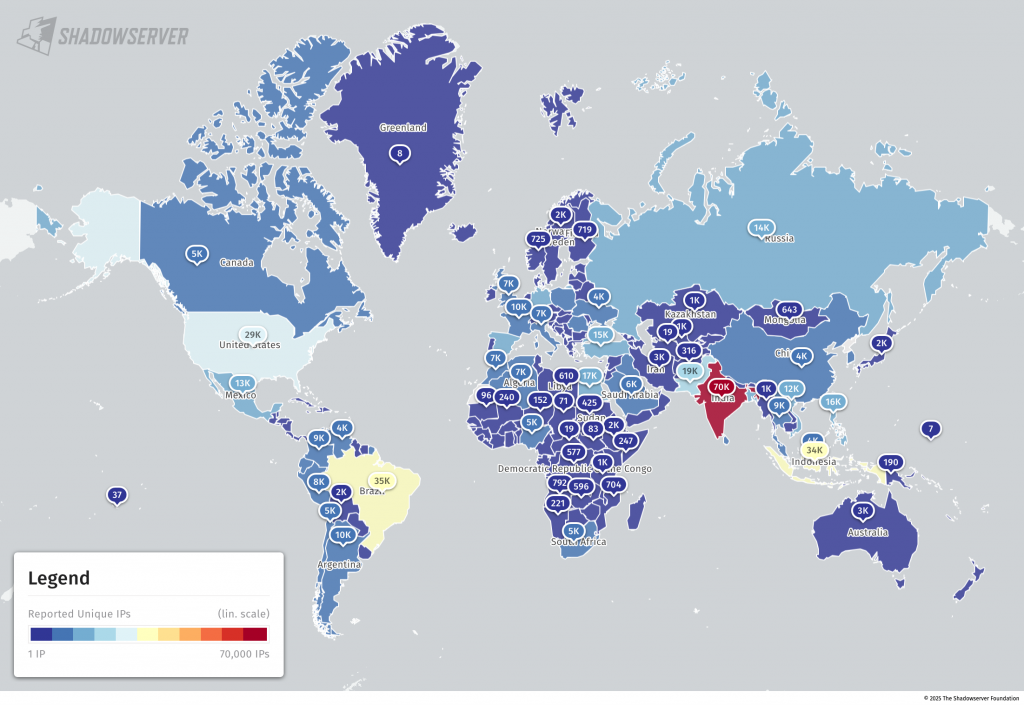
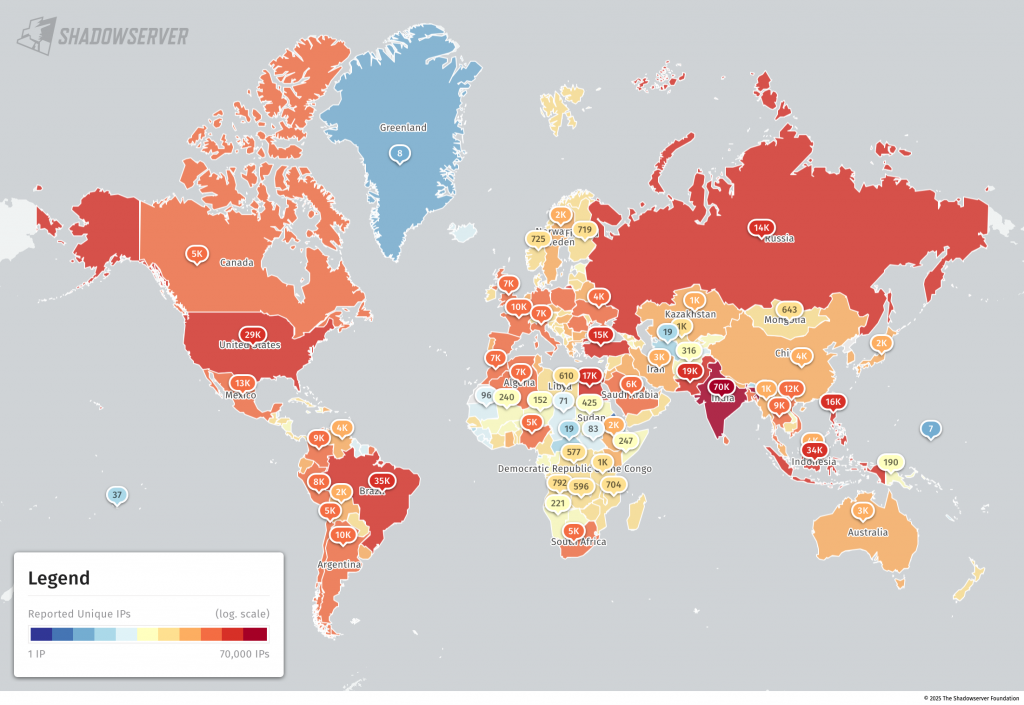
The world maps below show the total number of Rhadamanthys infections logged per country (updated to use the 2025-12-15 enhanced second Special Report data set):
(Rhadamanthys infections per country – linear scale. Links to public Dashboard 2025-11-12 and public Dashboard 2025-12-15 )
(Rhadamanthys infections per country – logarithmic scale. Link to public Dashboard 2025-11-12 and public Dashboard 2025-12-15)
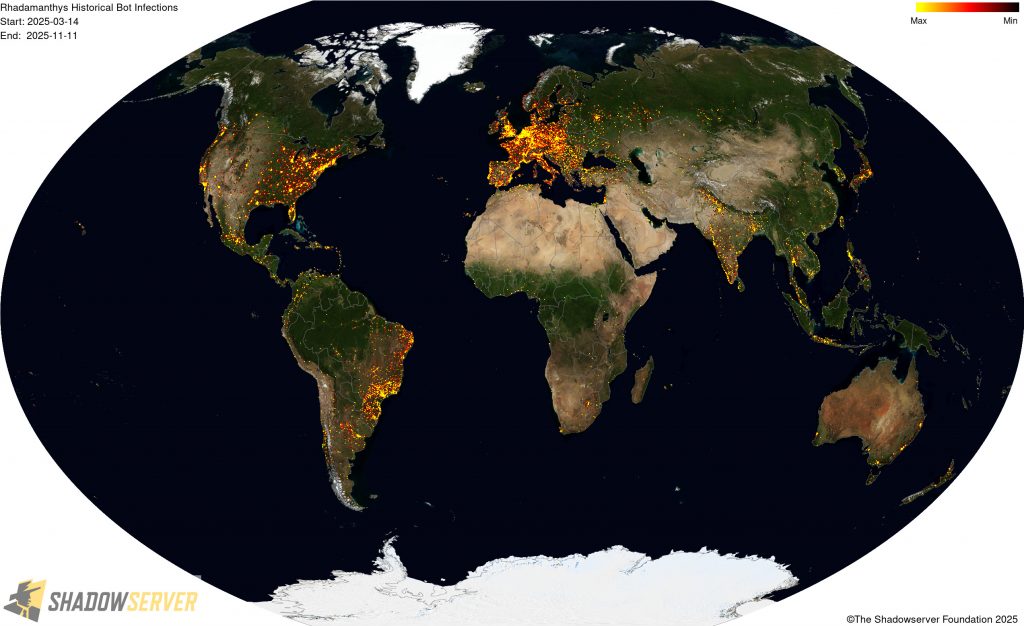
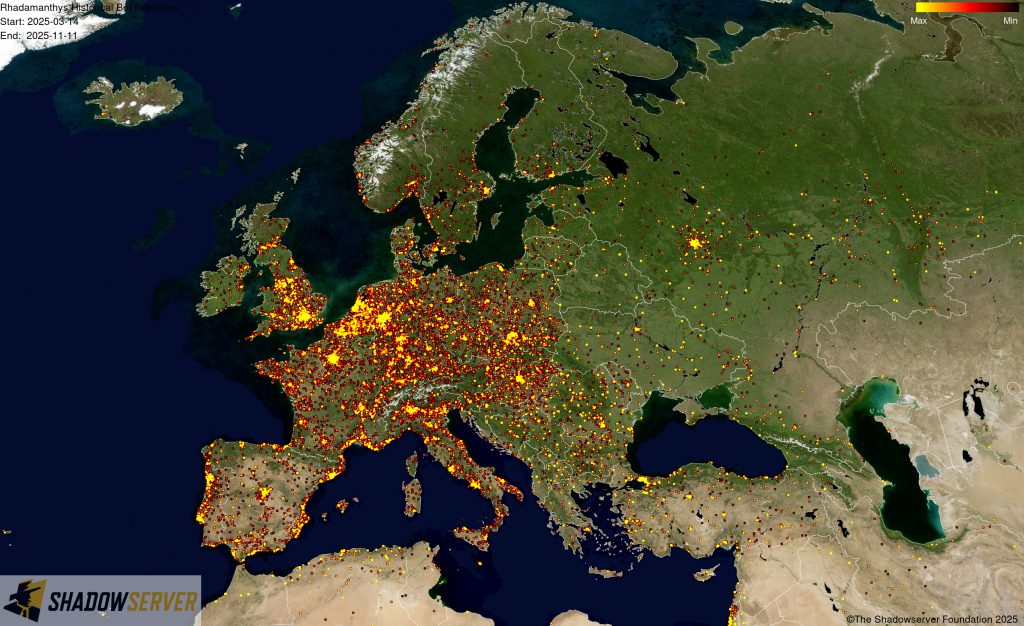
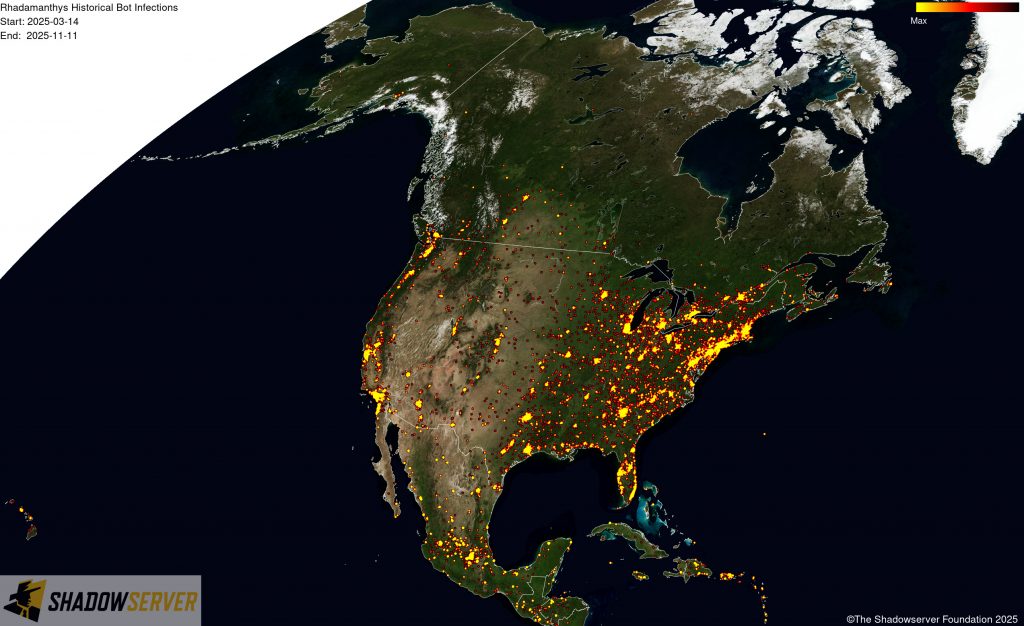
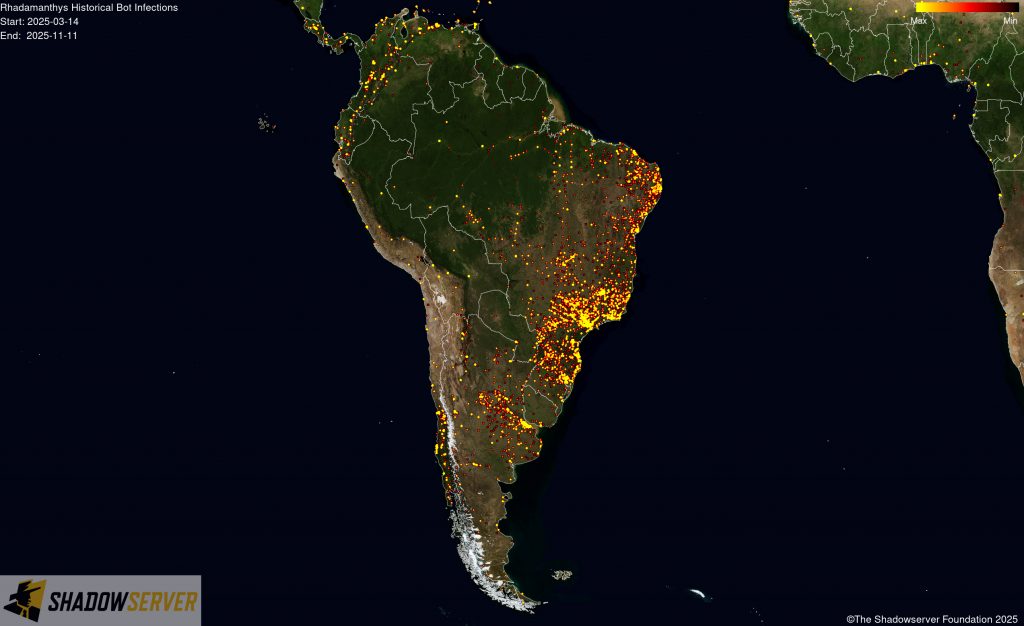
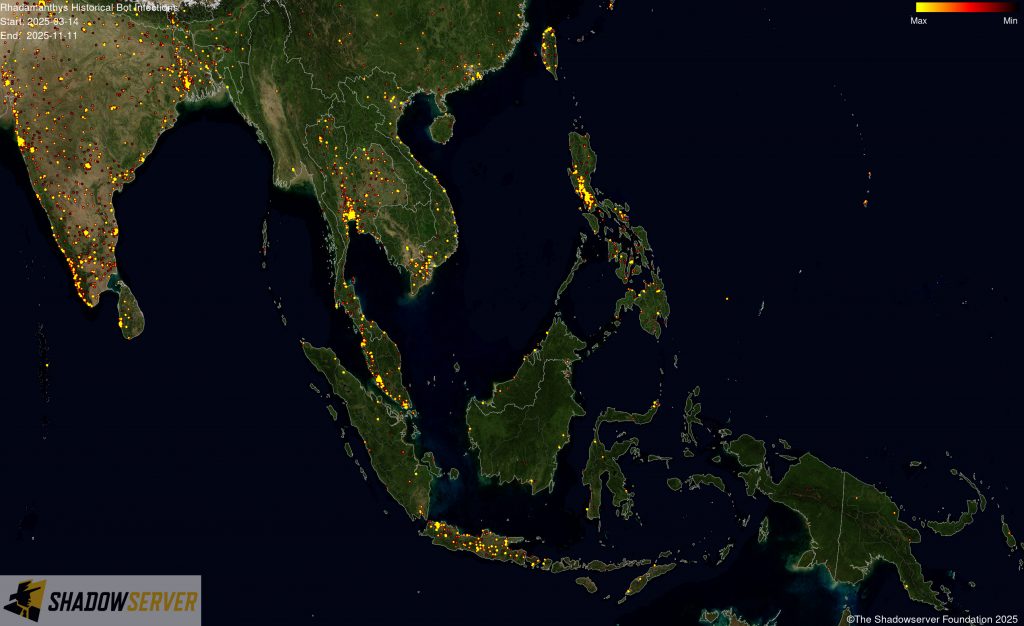
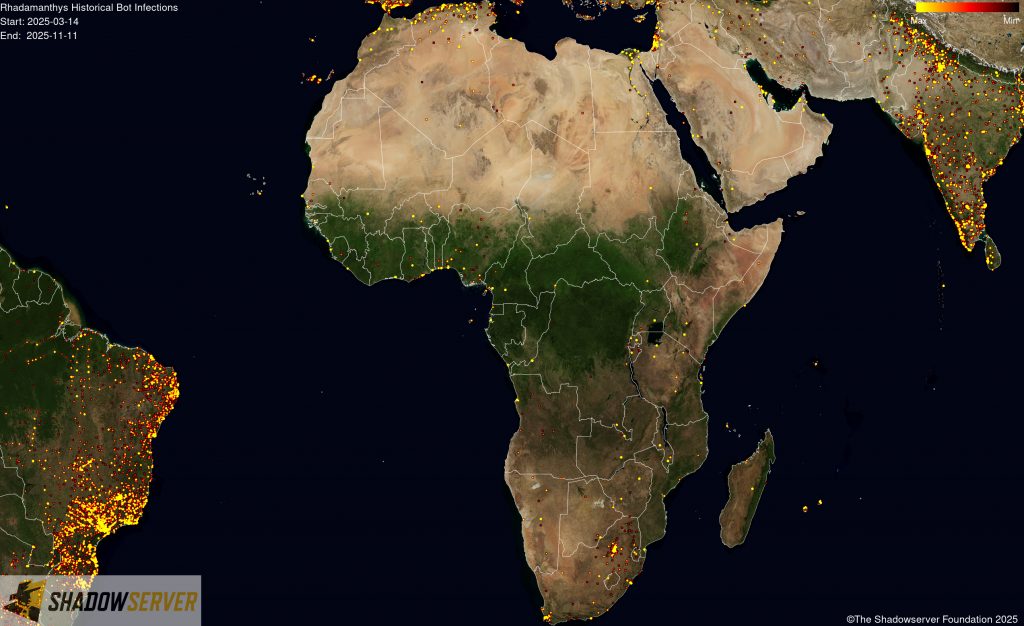
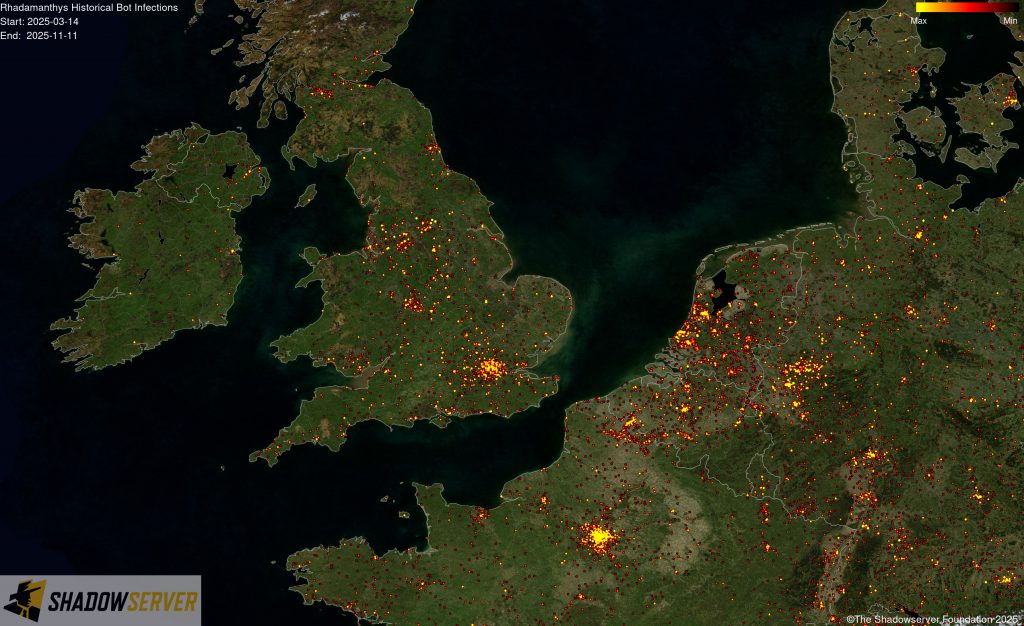
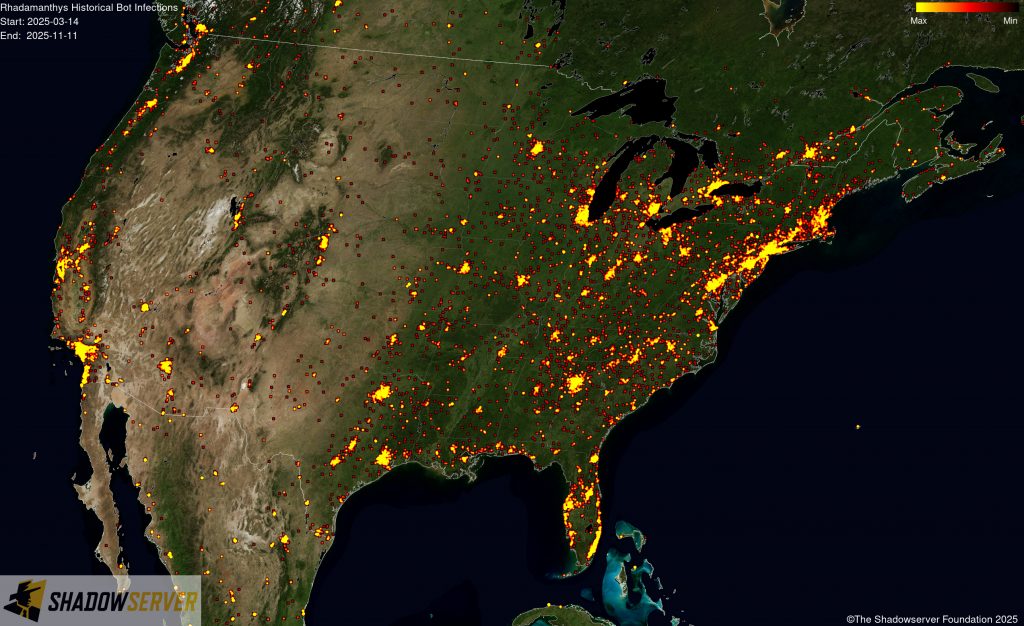
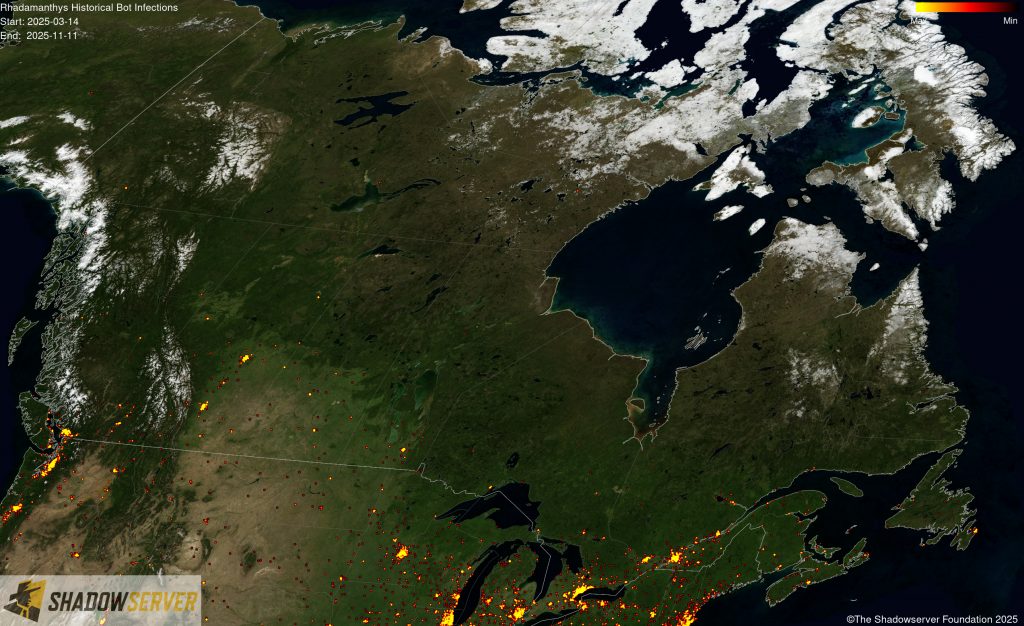
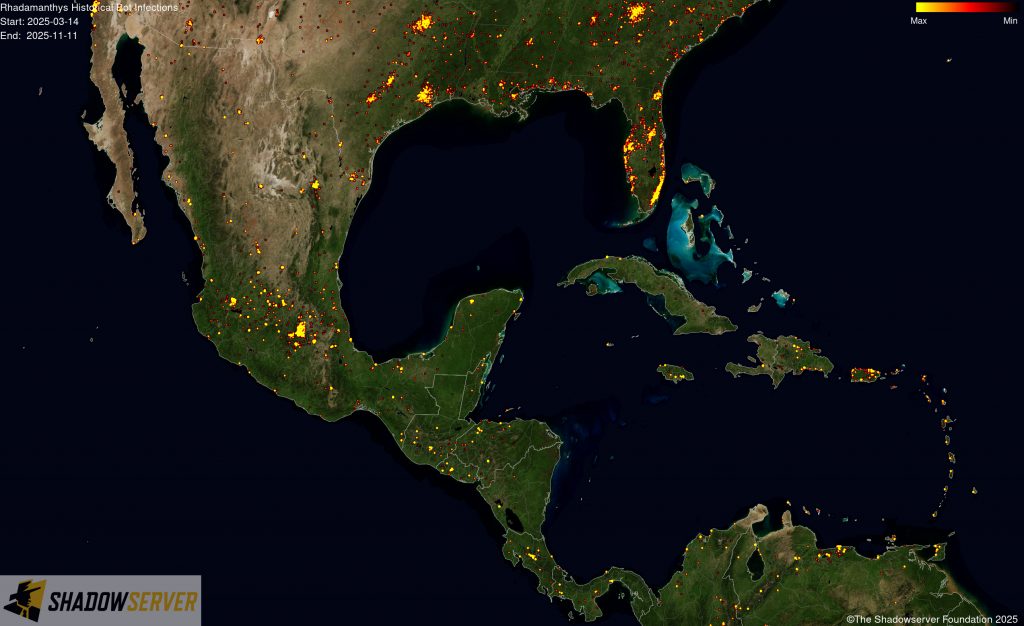
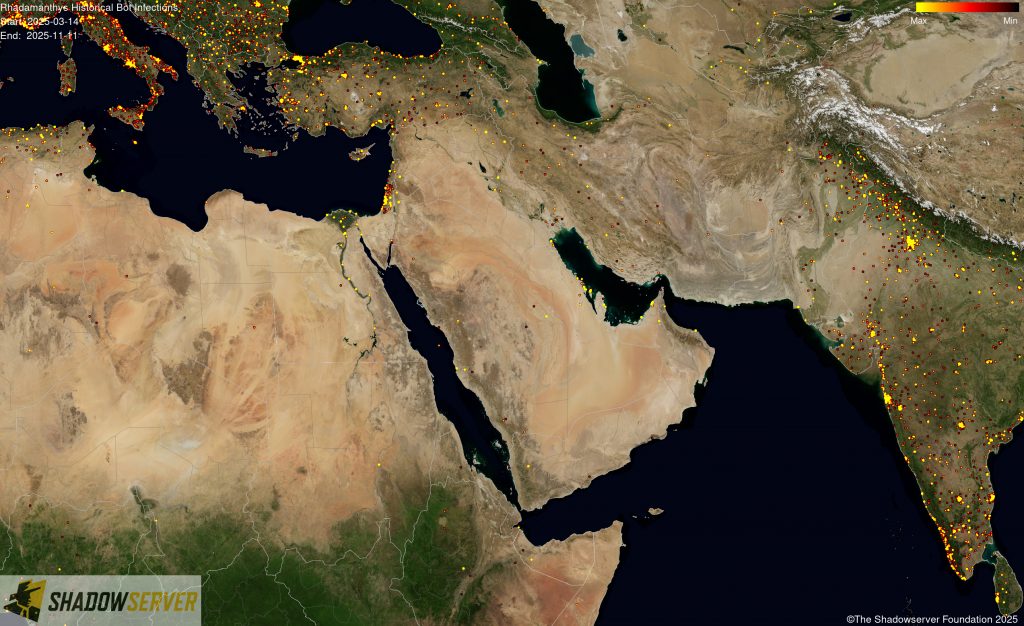
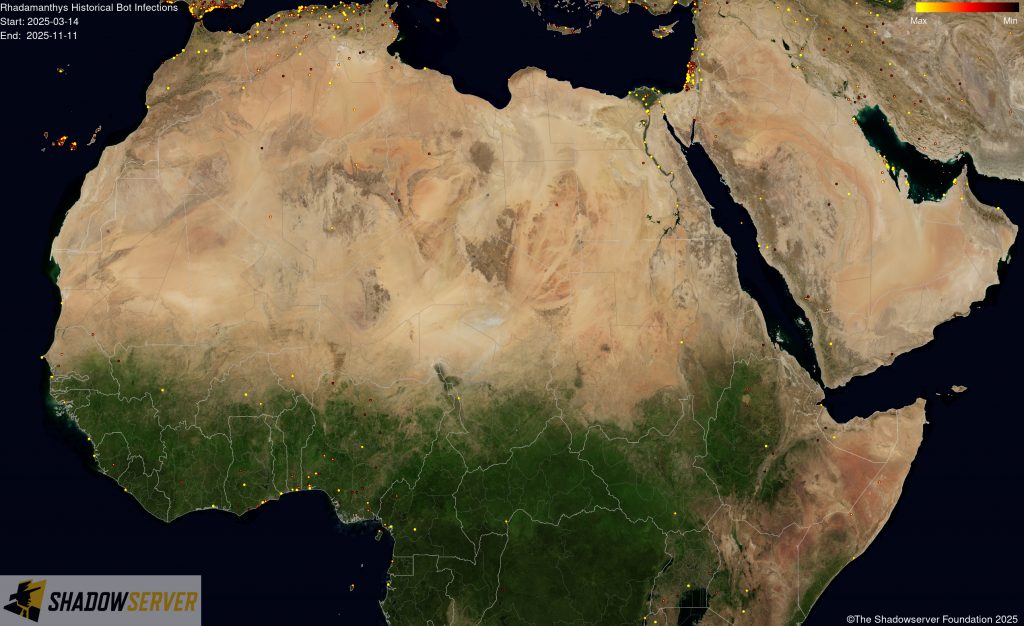
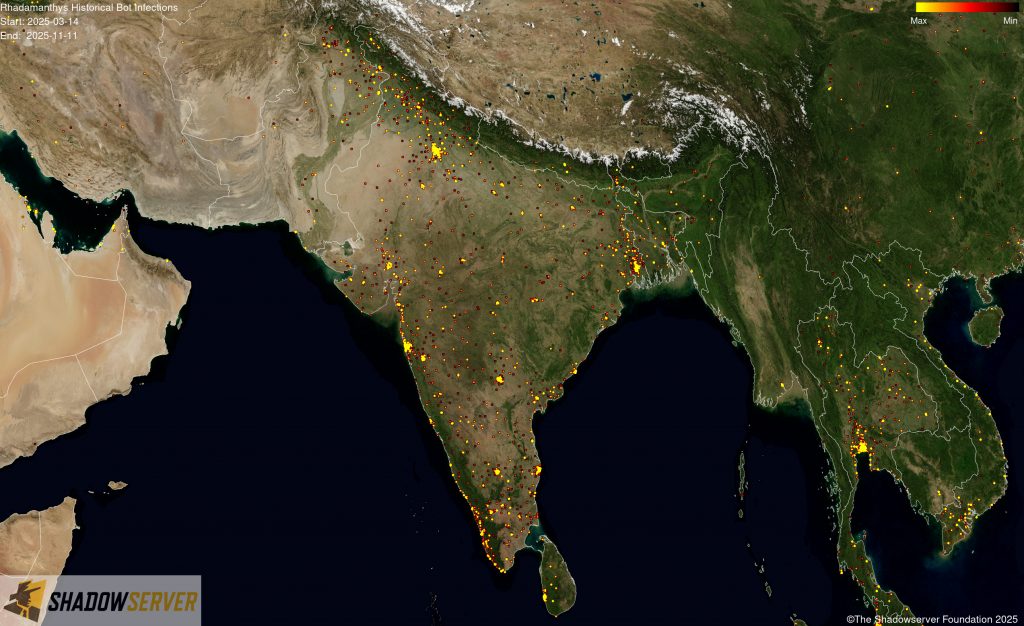
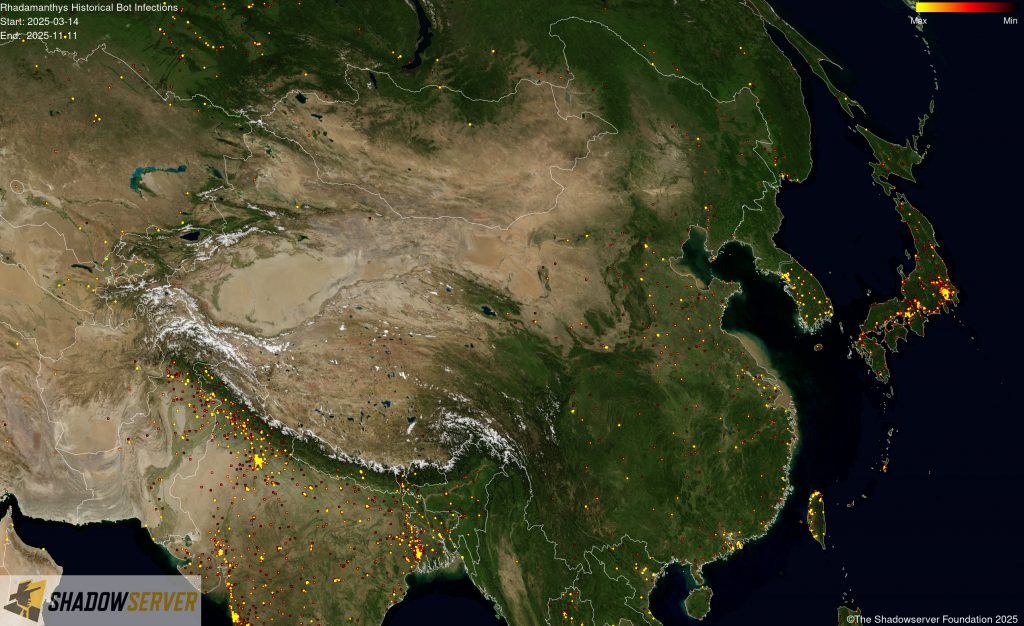
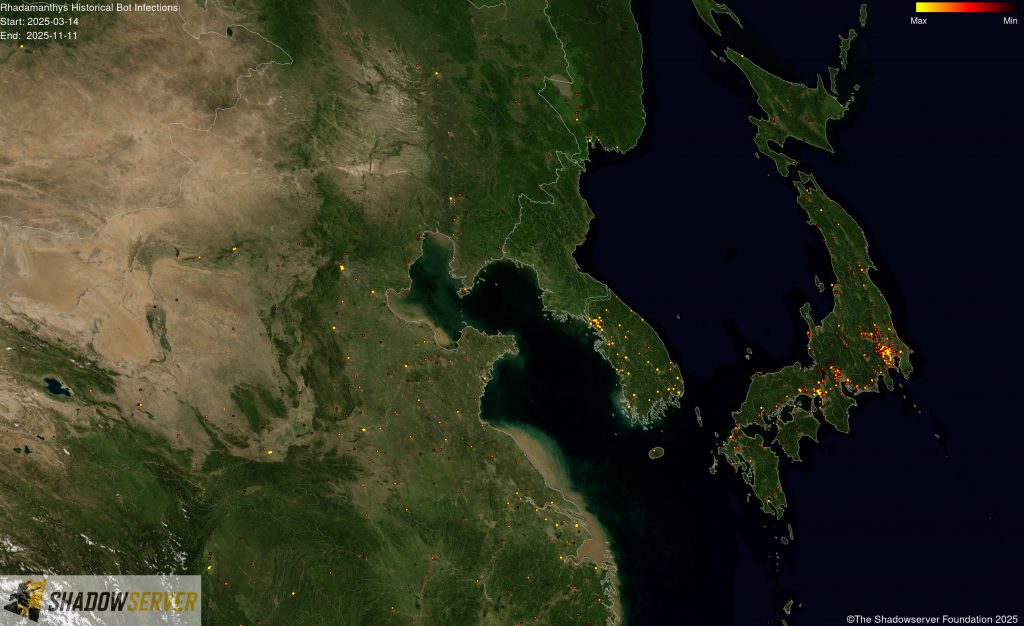
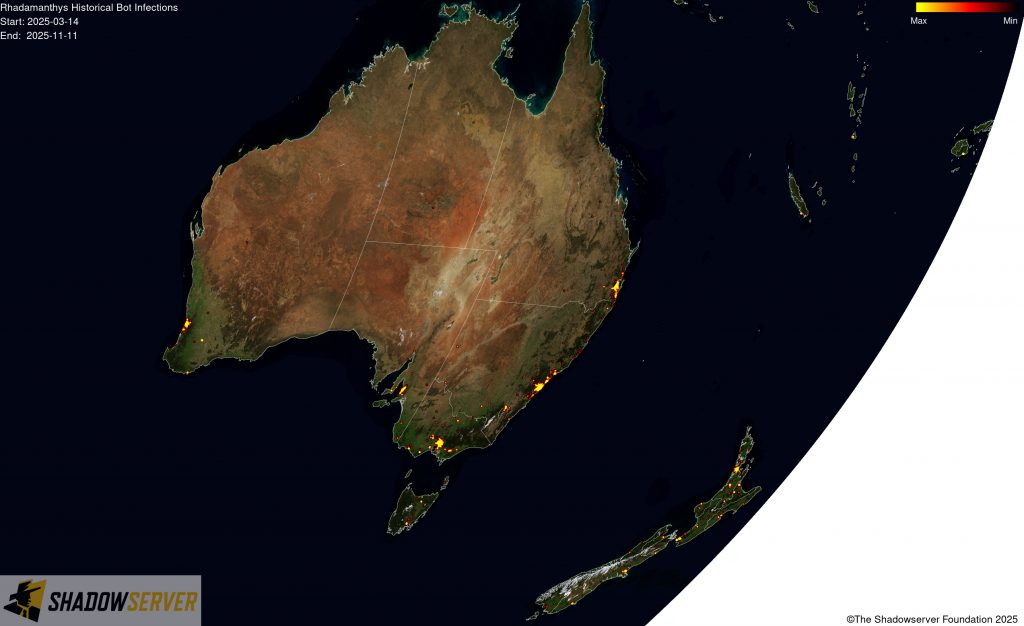
The IP-geolocated locations of each logged Rhadamanthys infection (note that since there can be multiple bot infections behind a single IP address, these visualizations show unique geolocated IP addresses and may therefore under-represent the actual victim distribution globally):
(IP-geolocated Rhadamanthys infections – Worldwide)
(IP-geolocated Rhadamanthys infections – Europe)
(IP-geolocated Rhadamanthys infections – North America)
(IP-geolocated Rhadamanthys infections – South America)
(IP-geolocated Rhadamanthys infections – East Asia)
(IP-geolocated Rhadamanthys infections – Africa)
(IP-geolocated Rhadamanthys infections – UK/Europe)
(IP-geolocated Rhadamanthys infections – Scandinavia)
(IP-geolocated Rhadamanthys infections – USA)
(IP-geolocated Rhadamanthys infections – Canada)
(IP-geolocated Rhadamanthys infections – Central America)
(IP-geolocated Rhadamanthys infections – Middle East)
(IP-geolocated Rhadamanthys infections – North Africa)
(IP-geolocated Rhadamanthys infections – India)
(IP-geolocated Rhadamanthys infections – China)
(IP-geolocated Rhadamanthys infections – Japan/Korea)
(IP-geolocated Rhadamanthys infections – Australia/New Zealand)
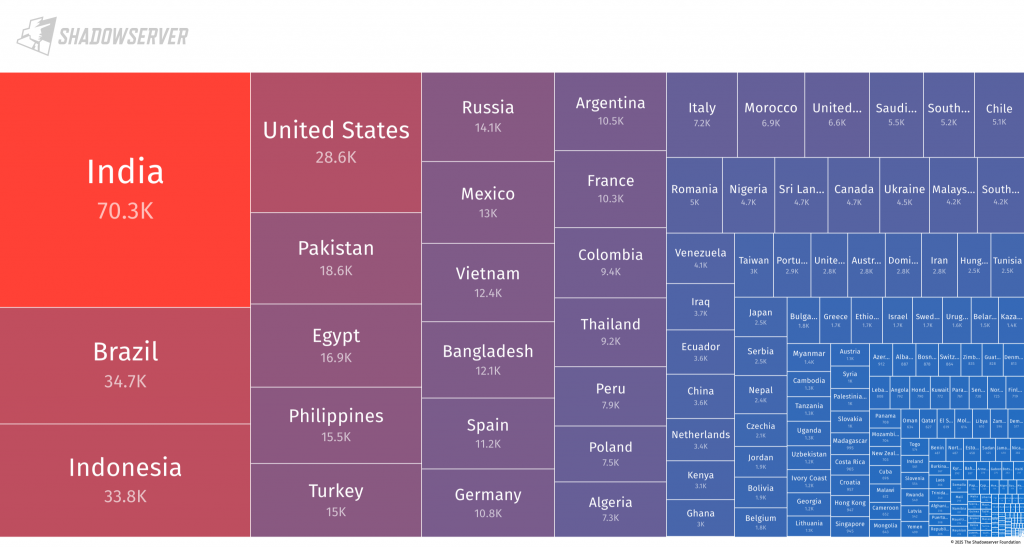
Looking at the data in a different way, the tree map below shows the relative ratio of Rhadamanthys infections logged per country to the total. Note that a small number (14) of IP addresses do not geolocate to a country, so the displayed number is slightly lower than the actual total:
(Rhadamanthys infections per country. Link to public Dashboard 2025-11-12 and public Dashboard 2025-12-15)
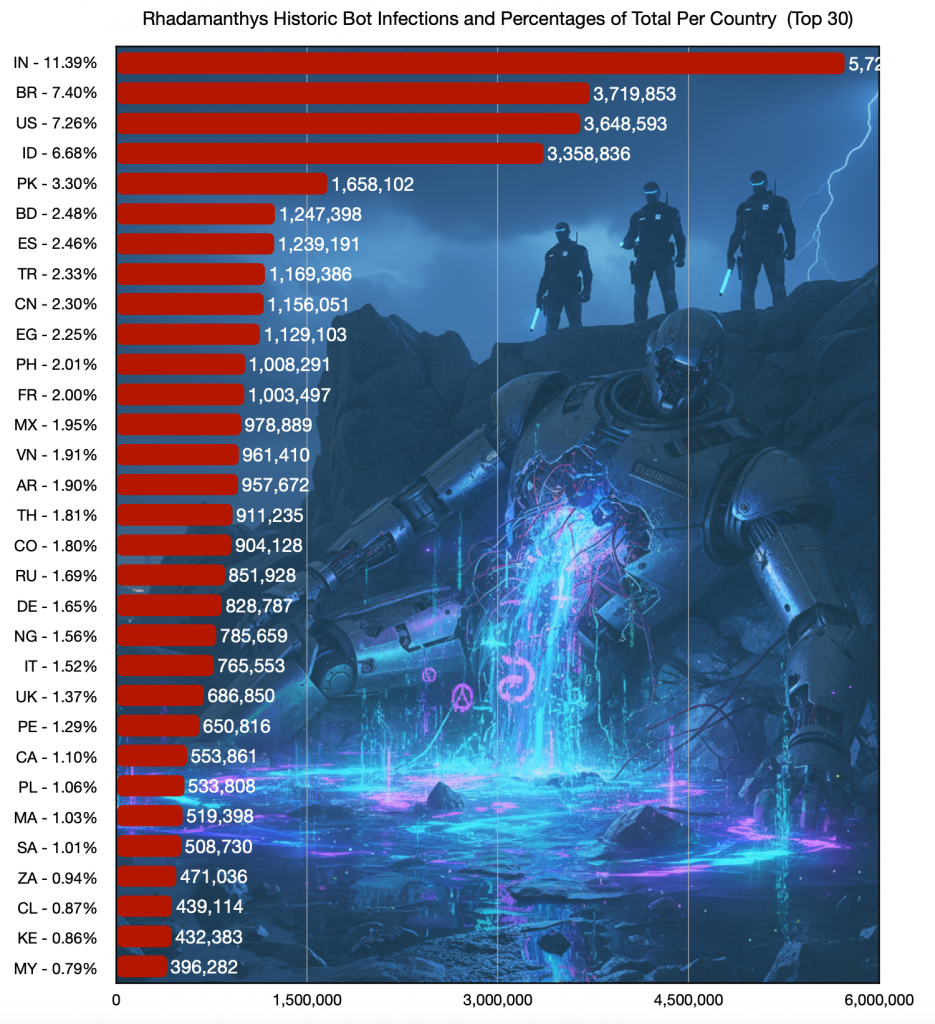
In chart form, the total number of Rhadamanthys infections logged during the period 2025-03-14 to 2025-11-11, and the percentage of the total per country, was:
(Rhadamanthys infections and percentage of total per country. Link to public Dashboard 2025-11-12 and public Dashboard 2025-12-15)
If you have any questions, please contact us, although there may be limitations on what information can be shared at this time due to the ongoing LE investigations.
Thank you to the UK Foreign, Commonwealth and Development Office (FCDO) and UK Integrated Security Fund (ISF) for supporting The Shadowserver Foundation’s public benefit mission and enabling us to continue to provide free support to our international Law Enforcement partners on another successful cybercrime disruption operation.