VPNFilter was publicly announced by the DoJ/FBI and Cisco Talos on May 23rd 2018, and refers to a multi-stage modular malware platform designed to infect small office and home office (SOHO) routers and other network devices. VPNFilter is believed to be operated by the Russian threat actor known as APT28 (also known as Pawn Storm, Sandworm, Sofacy Group, Sednit X-Agent and STRONTIUM), which is allegedly associated with the Russian military intelligence agency (GRU). Cisco Talos claimed to have observed over 500,000 infections in 54 countries. At the time of initial publication, there was a high focus of VPNFilter on Ukranian targets.
VPNFilter is believed to compromise SOHO networked devices manufactured by Asus, D-Link, Huawei, Linksys, Mikrotik, Netgear, QNAP, TP-Link, Ubiquiti, Upvel and ZTE (although the initially reported list of known impacted devices was smaller). The exact method of compromise is still unconfirmed, but is believed to include TCP port scanning and the exploitation of previously known vulnerabilities in the target devices.
Stage 1 of the infection involves installing a worm, which is specifically compiled for various MIPS and ARM hardware platforms which run the busybox operating system shell. Unusually for IoT malware, cross boot persistence is achieved by taking advantage of the busybox “cron” task scheduler, to allow the stage 1 worm to survive reboots. The running worm then attempts to download subsequent infection stages from remote URLs, or if that fails, falls back to listening on a network socket for remote commands.
Infection stage 2 is the core VPNFilter malware, with many common malicious technical features – such as file collection, command execution, data exfiltration and remote device management. Stage 2 also features the ability to remove the malware, plus a self destruction capability that can destroy the firmware of the device – potentially making it unusable (“bricking”).
The optional third stage of the infection is made up from specialist custom malware modules, such as industrial control system (MODBUS) monitoring, encrypted tor communications and sniffed credential exfiltration, and a more recently discovered webtraffic malicious content injector.
On May 23rd, the DoJ/FBI seized and sinkholed the VPNFilter C2 domain “toknowall.com“, while simultaneously compelling the image sharing site Photobucket to remove the user profile URLs also being used to link to the second stage VPNFilter malware components. The FBI advises users to perform a hard reset of infected or at risk devices, which will remove the non-persistent stage 2/3 malware, and leave the persistent stage 1 worm unable to re-download those modules. However, since the stage 1 worm will still be listening on a network socket, infected devices can still be remotely controlled by attackers (although with reduced Op Sec, due to the direct connection that is required). Firmware updates from vendors are therefore necessary to fully address VPNFilter, which may be unlikely for many poorly managed SOHO devices.
The data from the FBI’s sinkholing operation is available through the non-profit Shadowserver Foundation, who are distributing it to National CERTs and network owners globally for victim remediation. Currently, Shadowserver observes around 14,000 unique IP addresses associated with VPNFilter infections per day globally:
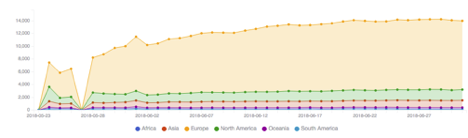
VPNFilter sinkhole statistics
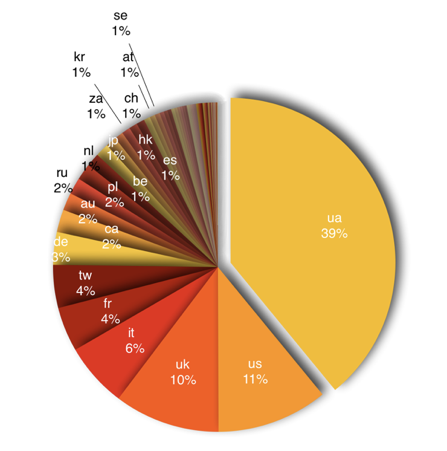
There is still a strong bias towards Ukraine, which has approximately half of the global VPNFilter infections:
VPNFilter sinkholed victim distribution globally
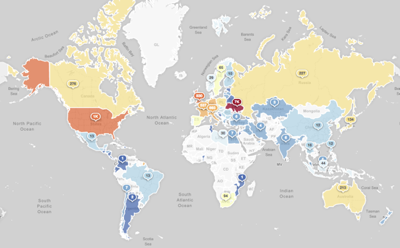
Distribution of IP geo-located sinkholed IP addresses to date:
VPNFilter IP geo-located sinkholed victim locations
Recommended Actions:
- Sign up for The Shadowserver Foundations free daily victim remediation feeds, to identify already infected devices.
- Reboot and patch all identified infected devices.
- Identify and patch all potentially at risk devices.
- Ideally remove any exposed remote management functionality that is not essential for production operation.

