DESCRIPTION LAST UPDATED: 2023-12-20
DEFAULT SEVERITY LEVEL: HIGH
This special report contains information about hosts that can be abused in a novel type of Denial-of-Service (DoS) attacks: loop DoS. Loop DoS becomes possible if two network services indefinitely respond to each other’s messages. The hosts contained in this file have been found to cause such endless loop patterns.
To illustrate the attack vector, imagine two DNS resolvers that respond with an error message when receiving an error message as input. If an error as input creates an error as output, and a second system behaves the same, these two systems will keep sending error messages back and forth — indefinitely. The figure below shows such an example we identified among real DNS servers. An attacker can cause a loop among two faulty DNS servers by injecting a single, IP-spoofed DNS server failure message. Once injected, the servers continuously send DNS error messages back and forth, putting stress on both servers and any network link connecting them.
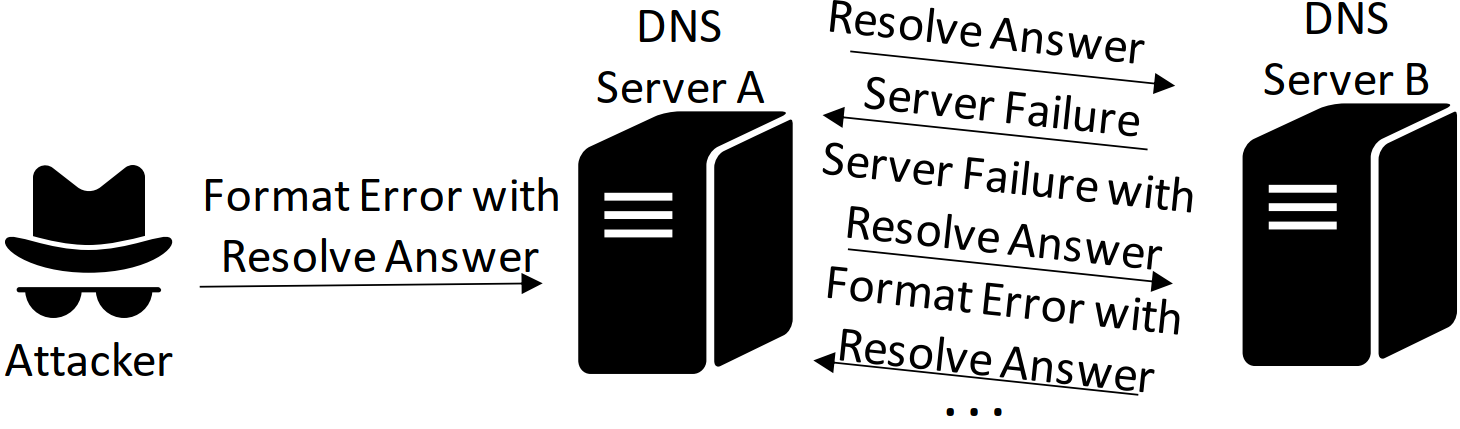
Loop DoS attack illustration
If you receive the report for your network, we would appreciate feedback as to the vendor/product involved. This is necessary for us to alert vendors to patch this vulnerability. You can report feedback via e-mail to loop-dos (at) shadowserver.org or simply Contact Us.
What are Shadowserver Special Reports?
Shadowserver Special Reports are unlike all of our other standard free daily network reports. They do not cover a specific daily 24 hour time period.
Instead, we send out Special Reports in situations where we are able to share one-time, high value datasets that we feel should be reported responsibly for maximum public benefit. Sometimes there are incidents when it would be useful to be able to notify potential victims about events or breaches that may have impacted them outside of the previous 24 hour period, when it may take a number of days for incident responders to conduct forensic investigations and analyzed data becomes available for sharing with potential victims. Although the events included in these Special Reports will fall outside of our usual 24 hour daily reporting window, we believe that there would still be significant benefit to our constituents in receiving and hopefully acting on the retrospective data.
If you have missed a Special Report because you were NOT yet a subscriber at the time a report was pushed out, simply subscribe for your network now and specifically request all recent Shadowserver Special Reports – and we will regenerate them specifically for your network, at no cost.
Note that the data shared across special reports may differ on a case by case basis, hence the report formats for different Special Reports may be different.
Severity levels are described here.
Filename prefix: 2023-12-19-special.

