Critical Apache ActiveMQ Vulnerability Exploited to Deliver Ransomware
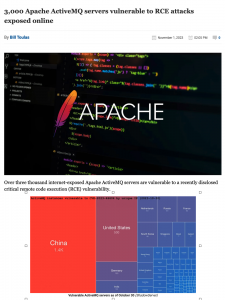
A recently patched vulnerability affecting the Apache ActiveMQ message broker is being exploited by cybercriminals in an apparent attempt to deliver ransomware. Apache ActiveMQ is described as the “most popular open source, multi-protocol, Java-based message broker”. Several 5.x.x versions of the product, as well as the Apache ActiveMQ Legacy OpenWire Module, are affected by CVE-2023-46604, a security hole that can be exploited for remote code execution. On October 30, the Shadowserver Foundation reported seeing over 7,000 internet-exposed ActiveMQ instances, including roughly 3,300 that had been vulnerable to attacks exploiting CVE-2023-46604.