Year 3 of Avalanche… the work quietly goes on even though the limelight has moved on.
We previously blogged in detail during 2016 and 2017 about the the successful takedown of the long-running criminal Avalanche double fast flux platform that was announced by a consortium of international public and private partners, including The Shadowserver Foundation.
To briefly recap: in year 1 (November 2016), we supported the German LKA, FBI and Europol in taking down the Avalanche malware delivery platform. This platform was responsible for delivering resilient command and control (C2) services for 20 different malware strains, all of which utilized Domain Generation Algorithms (DGAs). Whilst the Fraunhofer Institute (FKIE) took on the challenge of identifying all of the potentially viable domain names that might be utilized during the coming year, we worked to coordinate the means by which all of those domains might be legally or technically seized or blocked from issue. For Year 1 of Avalanche this amounted to some 832,000 domain names across 60 Top Level Domains (TLDs) in 57 jurisdictions. This remains to date possibly the most ambitious botnet takedown operation ever undertaken by Law Enforcement.
Success was achieved through a matrix of court orders (for jurisdictions where they were available) and with the cooperation of DNS registries around the globe, in the cases where judicial pathways were not possible. This joint action was facilitated by the trust and reputation of our fellow not-for-profit organization – The Registrar of Last Resort (RoLR) and the industry connections it has built since Shadowserver created it in 2014. Thanks to the incredible work of the LKA senior investigating officer in the case and the chief prosecutor from Lower Saxony (who went on to win the prestigious JD Falk award from M3AAWG for their tireless dedication on this case), the excellent work of the FBI and coordination from Europol and ICANN support, we eventually found or created the pathways necessary to deal with all of the TLDs and were able to ensure that, in parallel to infrastructure seizures during the action days, no remaining avenues were left for the criminals to control their infected bots.
In Year 2 (November 2017), we repeated the process, with the number of malware C2 domains that needed to be dealt increasing from 832,000 to 840,000 domains, due to the addition of the Andromeda botnet in its entirety when a parallel FBI/Microsoft investigation came to fruition. This resulted in some 2.5 million unique IP addresses hitting our combined sinkholes each day – demonstrating the extraordinary size of the many Andromeda botnets. Thanks to the combined Law Enforcement action, we are happy to say that every infected user was protected from further exploitation, and the Andromeda botnet was no longer able to do what it was designed to do – which was to distribute over 80 other families of malware to infected victims.
The hope was that after another year of remediation activities by international Law Enforcement, National CERTs/CSIRTs and network owners, further action in Year 3 would not be necessary. However, at the time of the Year 2 operation, we had not been able to acquire a specific .ru domain that had not been sinkholed, but had been removed from sale following earlier action. This domain came back onto the market and we were able to purchase it and point it at our sinkholes in August 2018. Immediately botnet traffic levels increased again and we recorded an additional 2 million+ unique IP addresses of victim bots trying to connect to that C2 individual domain. That extra insight helped persuade Law Enforcement to re-run the operation for a third year. This time it was not possible to get court orders generated in Germany, so the US DoJ/FBI stepped up and only court orders issued in the US were available to use in Year 3.
Thanks to the protocols, relationships and processes established over the previous two years we were able to reach out to registry operators in 78 TLDs, and with the help of ICANN, RoLR, Law Enforcement and supporting letters from the German prosecutor, gain control of a further 854,000 domains – bringing the total number of blocked or seized and sinkholed domains to over 2.4 million domains over the three years of effort.
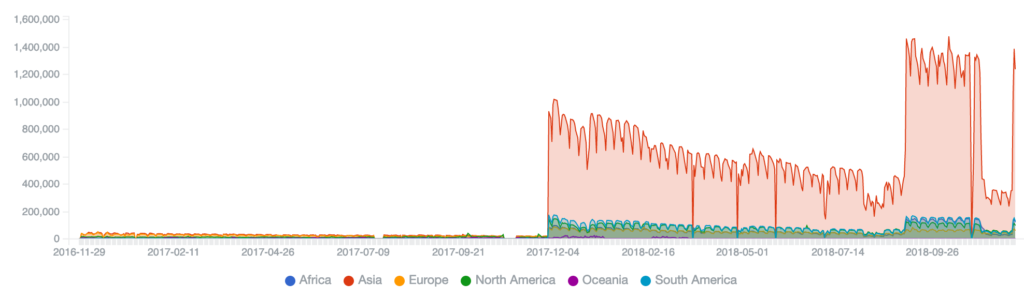
Avalanche/Andromeda Daily Sinkhole Statistics Years 1-3
Year 1: ~100K unique IP addresses per day
Year 2: ~1.3M unique IP addresses per day, with addition of Andromeda botnet
August 2018: Identified additional Andromeda victims with registration of single .ru domain, taking daily sinkhole infections to over 2M unique IP addresses again (domain temporarily lost Oct-Nov 2018 due to erroneous Russian abuse report)
Year 3: Normal service resumes. Currently ~1.6M unique victim IP addresses protected from criminal control per day
Andromeda bot infection counts remain high and the decay curve or remediation disappointingly slow – but we can be content that for at least 3 years now we have been able to deprive criminals of access to the malware strains previously deployed and operated through the Avalanche platform.
Sinkhole data from the Avalanche platform is available each day in Shadowserver’s free of charge daily reports to national CERTs and network owners.
Here is the global distribution of Avalanche related malware as of 2018-12-01:
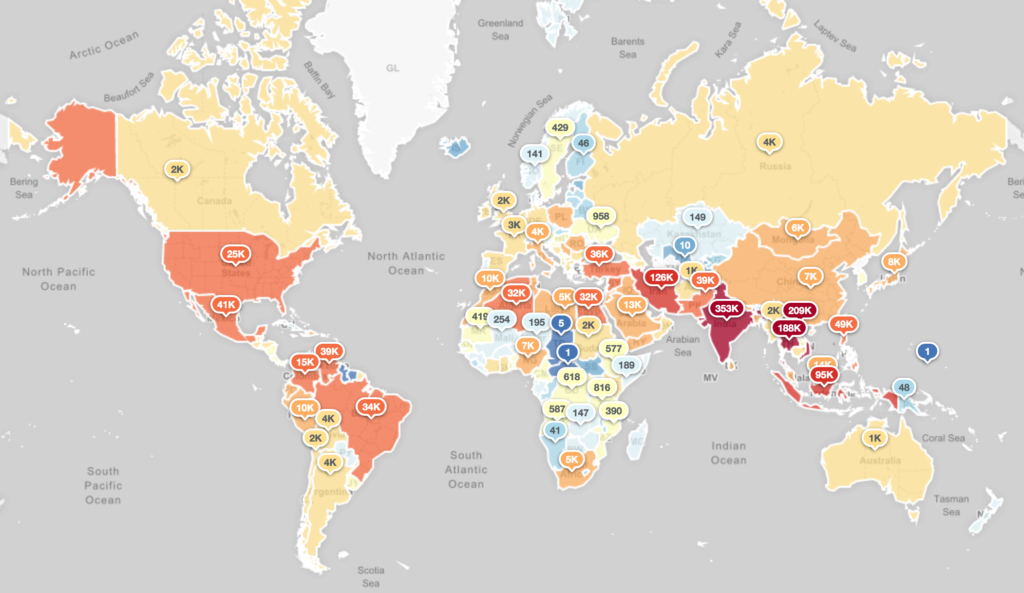
Avalanche/Andromeda victim infections – Year 3 Operation Day 20181201
Credit must be given to those who worked so hard on this case over the years from the German LKA and Lower Saxony Prosecutors’ Office, FBI and DoJ, Europol, Fraunhofer (FKIE), RoLR and Microsoft for their work on Andromeda (aka Gamarue).

